Article
New Account Fraud: How Can Fintech and Banks Prevent It?
Uros Pavlovic
April 4, 2024

New account fraud continues to pose a major challenge for fintech companies and financial institutions. Unlike account takeover attempts that target existing customers, this type of fraud begins at the very first digital interaction: account creation. Whether fraudsters use synthetic identities or stolen personal details, the goal is the same—create an account that looks legitimate enough to pass initial checks and slip through unnoticed.
Standard onboarding processes often rely on limited inputs: a valid-looking phone number, an email address that isn't obviously fake, or, when required by regulators, a piece of ID that appears authentic. These checks may meet basic compliance requirements, but they aren’t built to reveal who is truly hiding behind a set of contact details at the moment of sign-up.
This is where identity intelligence and digital footprint analysis become critical. These checks don’t take what a user claims at face valuedepend on what a user claims, but analyze the digital trail surrounding that claim for validation. Signals such as phone activity history, email behavior, IP consistency, and device specifications can uncover risk patterns that would be otherwise overlooked. Instead of validating fields in a form, identity intelligence examines whether the full picture makes sense.
The state of new account fraud in 2024–2025
In recent years, fraudulent account creation has scaled in both volume and sophistication. As customer acquisition moves increasingly online, fraudsters have adapted their strategies to exploit weak onboarding checkpoints—often by using tools that mimic real users with impressive accuracy.
Consider these recent developments:
- Scammers are increasingly leveraging artificial intelligence to create convincing fake identities, enabling them to open fraudulent accounts with ease. These AI-enhanced tactics have led to a notable rise in successful fraud attempts, challenging traditional verification methods (Source: WSJ).
- In the UK, fraud accounts for over a third of all crime perpetrated in England and Wales, causing losses for an estimated £460mn last year (Source: TheBanker).
- Australian banks reported over 100,000 accounts being exploited for money laundering activities in the past year. These so-called 'mule accounts' are often established using stolen or synthetic identities, highlighting the challenges financial institutions face in detecting fraudulent account openings (Source: AFR).
These cases demonstrate how easy it has become to create accounts that appear entirely legitimate until damage is done. What they also have in common is that surface-level data (such as registry entries, email addresses, or public-facing websites) failed to reveal the underlying deception.
The risk is clear: when verification processes rely solely on what a user inputs, rather than how that data behaves in context, fraud slips through unnoticed. Identity intelligence aims to close that gap.
Common fraud signals during account creation
Fraud rarely announces itself. Instead, it shows up through inconsistencies—small, often overlooked clues that, taken together, suggest something is off. During account creation, these clues are often tied to the user’s contact details, technical environment, and behavioral patterns.
To detect new account fraud early, businesses need more than email deliverability or IP reputation checks. They need visibility into the history and digital context of each input provided by users. The table below highlights several high-impact fraud signals and how identity intelligence solutions like Trustfull help bring them into focus:
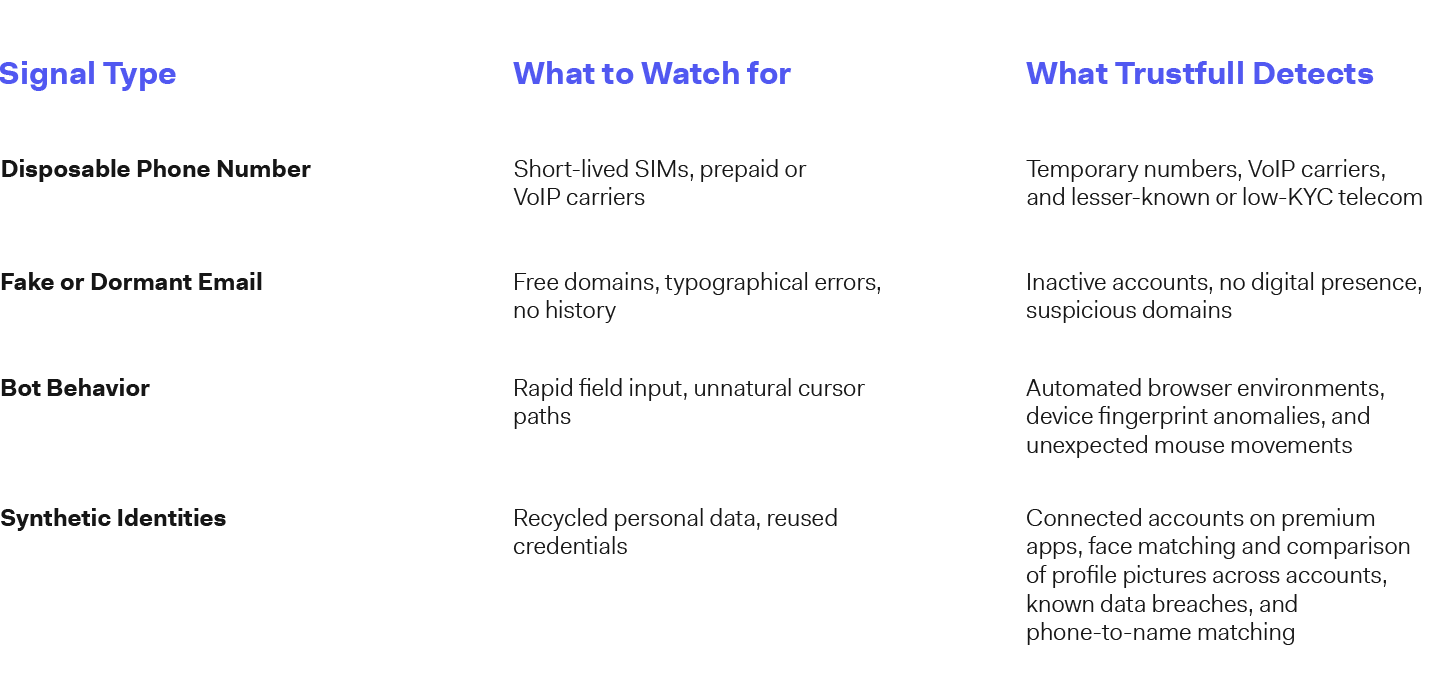
Each of these signals, in isolation, may seem harmless. But when observed together—or in combination with behavioral or device-based cues—they often reveal a pattern consistent with high-risk or fraudulent activity.
Identity intelligence doesn’t stop at validating data formats. It focuses on how believable that data is in context, and whether it aligns with the patterns of a real person, not just a working phone number or a deliverable email.
Detecting disposable phone numbers
Phone numbers are still a default identifier for many digital onboarding flows, but their reliability as a fraud signal has weakened. Inexpensive and widely available virtual numbers allow fraudsters to sign up at scale using temporary, untraceable contact points. These numbers are often issued through VoIP services or lesser-known telecom providers. Many are used once and abandoned, or cycled through across multiple accounts. The result is a clean-looking phone number with no behavioral history, offering just enough plausibility to bypass surface-level validation.
This is where identity intelligence makes a difference. Rather than treating all valid phone numbers equally, it assesses:
- Whether the number was recently activated
- The type of operator and geographic origin
- Patterns of short-term usage associated with known fraud tactics
Spotting these characteristics early helps fintechs and financial institutions stop fake accounts before they reach KYC or funding stages. It also removes the dependency on phone verification as a trusted step when the signal itself may be compromised.
Identifying fake and dormant email accounts
Email addresses remain central to account creation, password resets, and identity confirmation—but like phone numbers, not all of them tell a trustworthy story. Fraudsters often rely on:
- Disposable or temporary email services
- Accounts tied to free domains with no visible ownership
- Addresses that exist but show little or no history of use
These signals can be hard to catch using standard validation tools, which only check format or domain deliverability. What’s missing is context. Methodic digital footprint analysis fills that gap by examining traits like:
- Domain age and legitimacy (e.g. is it linked to a real business?)
- Signs of active usage, such as historical login patterns or breach exposure
- Connections between the email address and suspicious online behavior
When this layer is added, email stops being a static credential and becomes a source of insight. It reveals whether the contact belongs to a real user—or just a placeholder created to pass sign-up.
Spotting bots before they register
Not every fraudulent account starts with a human. Increasingly, attackers deploy automated scripts or bots to generate high volumes of sign-ups in a short period. These attacks aren’t just about speed—they’re built to mimic real users closely enough to slip past basic checks.
Automated sign-ups often exploit platforms that rely heavily on static and isolated input validation. Form fields are filled with synthetic identities, disposable contact details, and pre-structured data that looks legitimate on the surface. Without more advanced signals in place, it becomes difficult to distinguish human activity from automation. This is where behavioral analysis and device intelligence prove valuable. Subtle indicators—such as repeated timing intervals, lack of cursor movement, or browser environments associated with automation frameworks—can expose the presence of bots before accounts are created.
What makes these signals effective is that they don’t rely on blocking entire user segments or increasing friction for everyone. Instead, they detect small irregularities in how users interact with a page, whether through devices, browsers, or networks. These inconsistencies often go unnoticed in standard fraud prevention systems, but identity intelligence is built to surface them. Stopping bots before they register is really about protecting downstream systems from being overwhelmed by fake activity. That includes promo abuse, bonus farming, and more sophisticated types of synthetic fraud that begin with one quiet, automated signup.
The role of digital signals in business account opening protection
While new account fraud is often discussed in the context of consumer onboarding, B2B fintech companies are also experiencing a sharp rise in this type of fraud. Identifying fraudulent business accounts requires slightly different steps, but the core principle of prevention remains the same as with retail customers: verifying the authenticity of the user and their intentions. This means going beyond surface-level information to detect fake sign-ups, whether they involve synthetic identities or counterfeit businesses. In both cases, the key lies in analyzing a client’s digital footprint and hidden risk signals rather than simply accepting submitted information at face value.
For business verification and corporate onboarding, the starting point is usually the company registry of the country where the business is registered in. While these are viewed as official sources of information, if used in isolation, they often fail to reveal the full picture and truly validate the legitimacy of a business.
A growing number of synthetic business accounts are structured to pass registry checks while lacking any meaningful digital presence. These operations often mimic real companies or create entirely fabricated businesses, complete with copy-paste websites and generic contact points.
Web presence screening helps fill that verification gap. When used as part of a broader KYB process, domain intelligence makes it possible to assess whether a business exists beyond the registry and whether it’s behaving like an active entity.
Some of the key signals to assess include:
- Domain age and registration transparency – newly registered domains or privacy-protected ownership records can point to suspicious intent.
- Website structure and metadata – thin or templated content, missing legal pages, and reused assets can all raise red flags.
- Digital footprint consistency – does the business have a traceable presence across directories, social media, or search engines?
- Contact alignment – do listed emails and phone numbers align with the domain and industry, or do they appear generic?
These checks don’t replace official KYB obligations—they support them. In industries where onboarding the wrong business can lead to fraud exposure, reputational damage, or compliance failures, verifying the legitimacy of a web presence can offer a more complete picture of risk.
How does Identity Intelligence mitigate new account fraud?
Preventing new account fraud is about interpreting the right signals early, before a bad actor can complete onboarding. This is where Identity Intelligence adds that necessary early layer of defense without increasing friction or burdening users with additional steps. Instead of focusing on specific inputs in isolation —like an email address, a phone number, or a government-issued ID—identity intelligence considers what those details reveal about a user or business, providing a holistic assessment of each new signup.
Is this phone number active and legitimate? Has the email been seen across other accounts? Does this behavior resemble that of a real person or something scripted?
When these signals are evaluated together, they create a broader understanding of intent and legitimacy, one that goes beyond formatting checks or blacklists. And because this analysis happens quietly in the background, it allows financial institutions and fintech companies to build safer onboarding flows without degrading the user experience.
Trustfull helps bring these insights into focus. Through phone and email intelligence, bot detection, and digital footprint analysis, platforms can make faster, more confident decisions and keep fraud out before it becomes fraud at all.


