Referral & promo abuse
Win against incentive abuse
Referral and promo abuse at a glance

Frictionless protection against referral and promo abuse
Promo policy protection
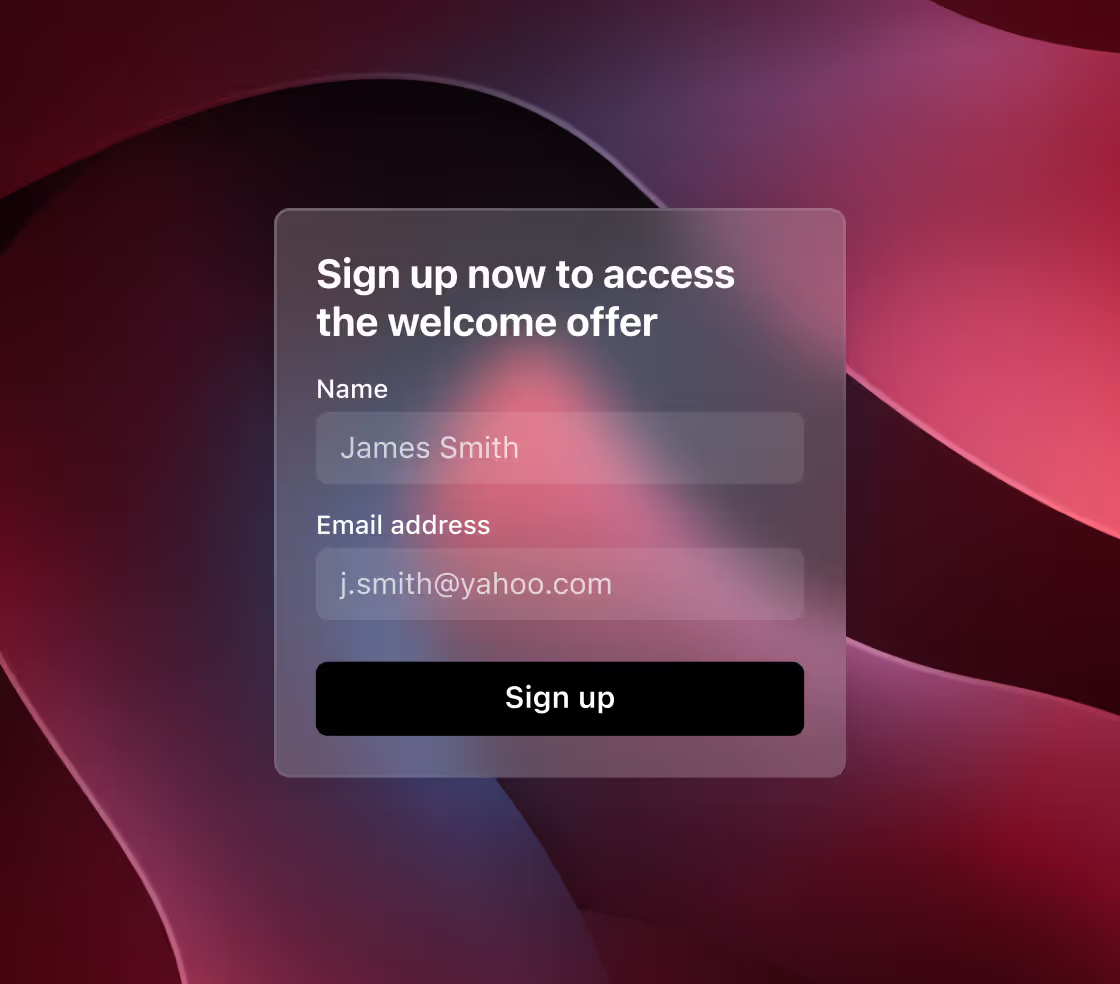
Protect the integrity of your customer acquisition programs from fake sign-ups.
Real-time detection
Instantly identify suspicious users and stop welcome bonus abuse before it’s too late.
Frictionless checks
Let legitimate users enjoy a smooth experience while abusers get stopped at the door.
Global coverage
Focus on growing safely across borders with our API’s full international coverage.
“At Snaitech we are actively investing in new technology that enables better customer journeys while increasing our defences against bad actors. After very successful testing with Trustfull, we decided to partner with them.”
Alessandro Graziosi
Chief Digital Officer - Snaitech


Frequently asked questions
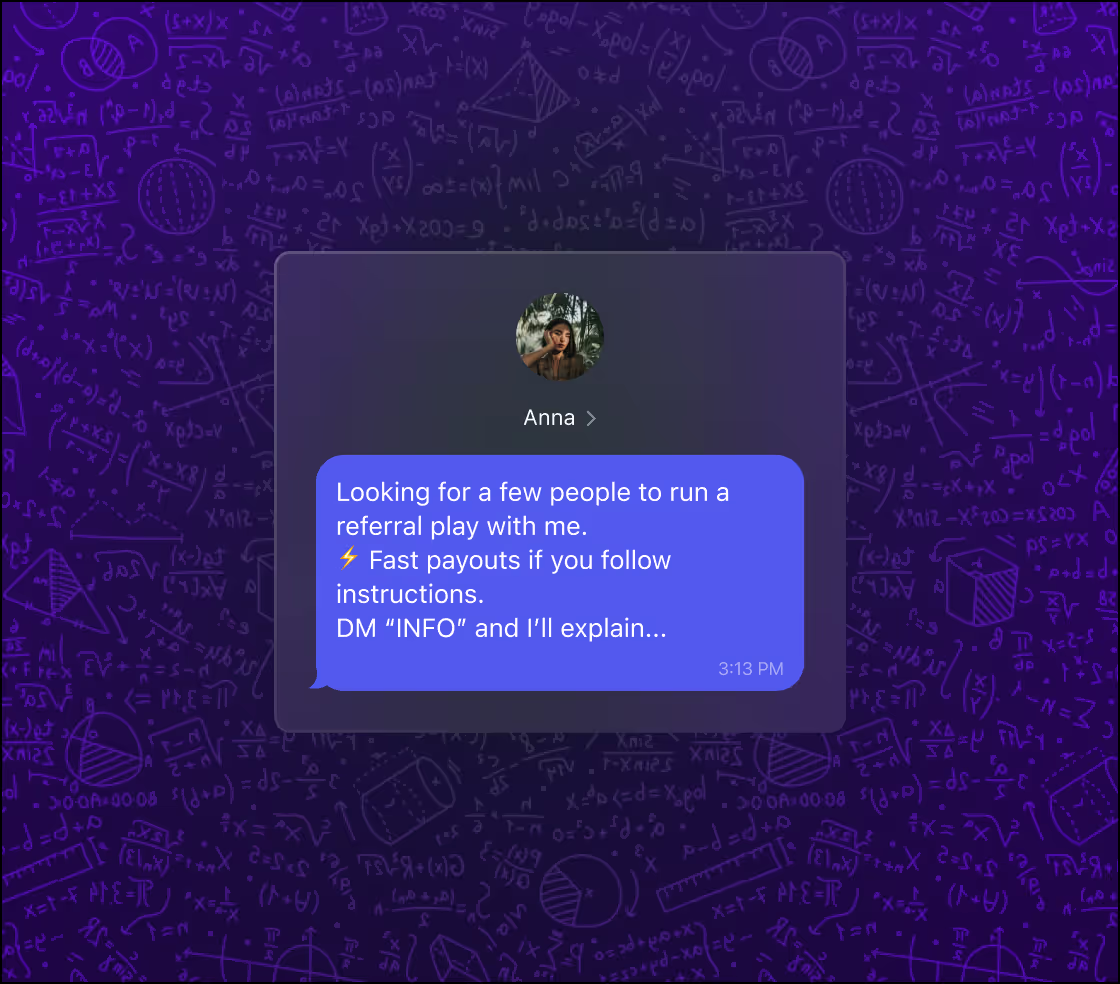
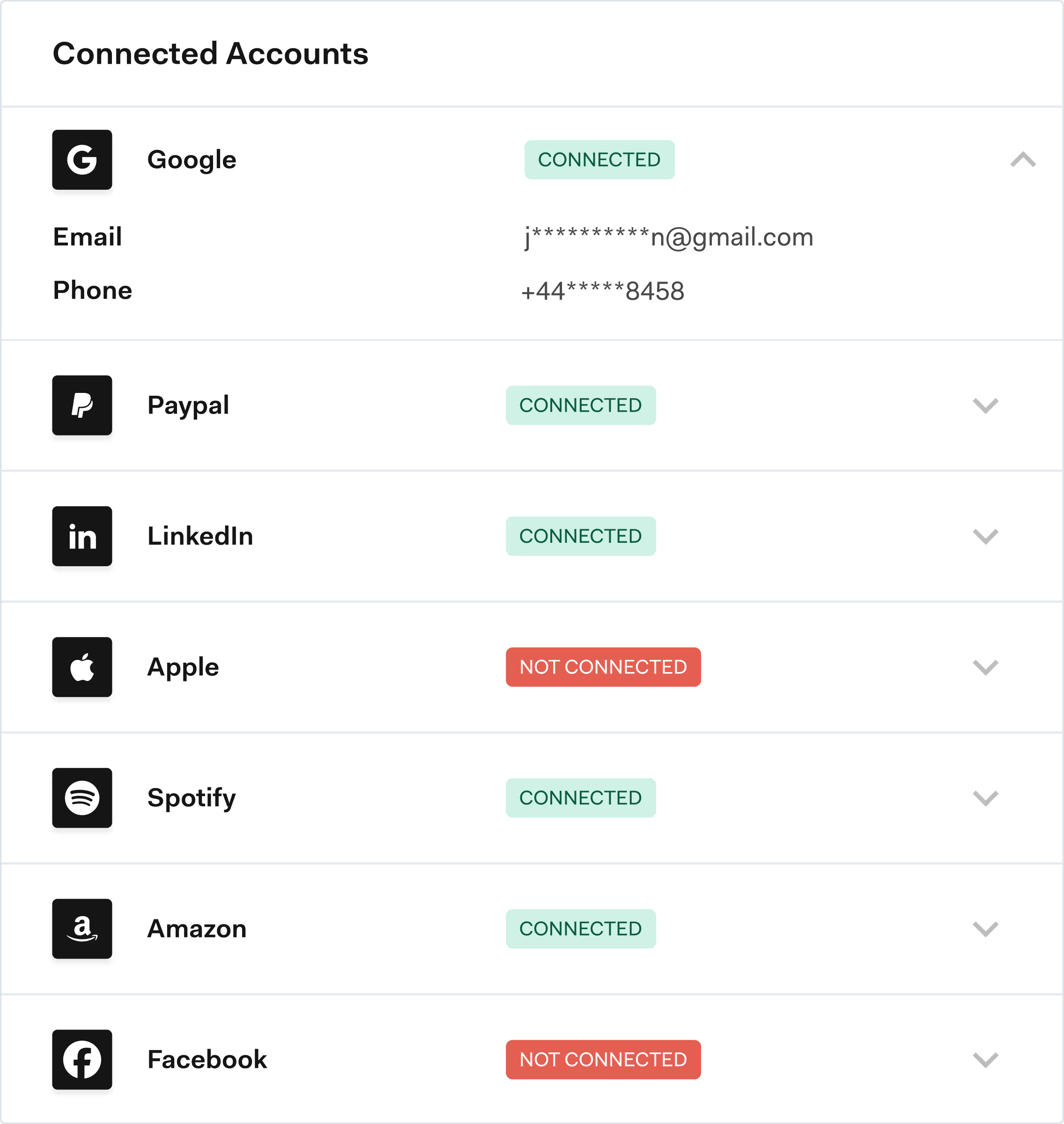
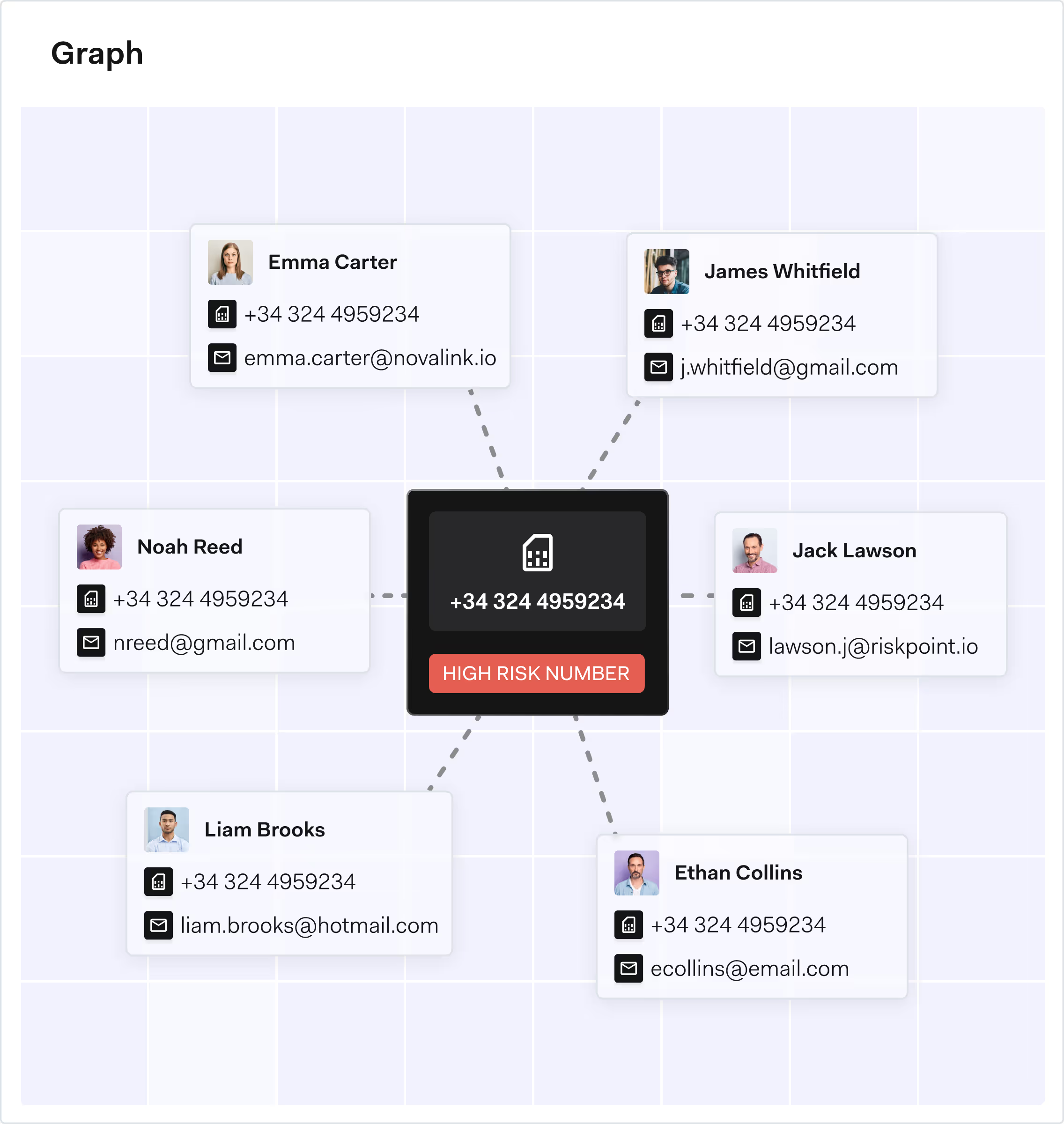
Multi-accounting is when a single person or fraud ring controls many different accounts, often using disposable emails, virtual phone numbers and spoofed devices. These accounts are then used to refer each other, unlock “new user” promos multiple times, or stack rewards that should only be earned once per real customer. Multi-accounting is one of the main engines behind referral and promo abuse.
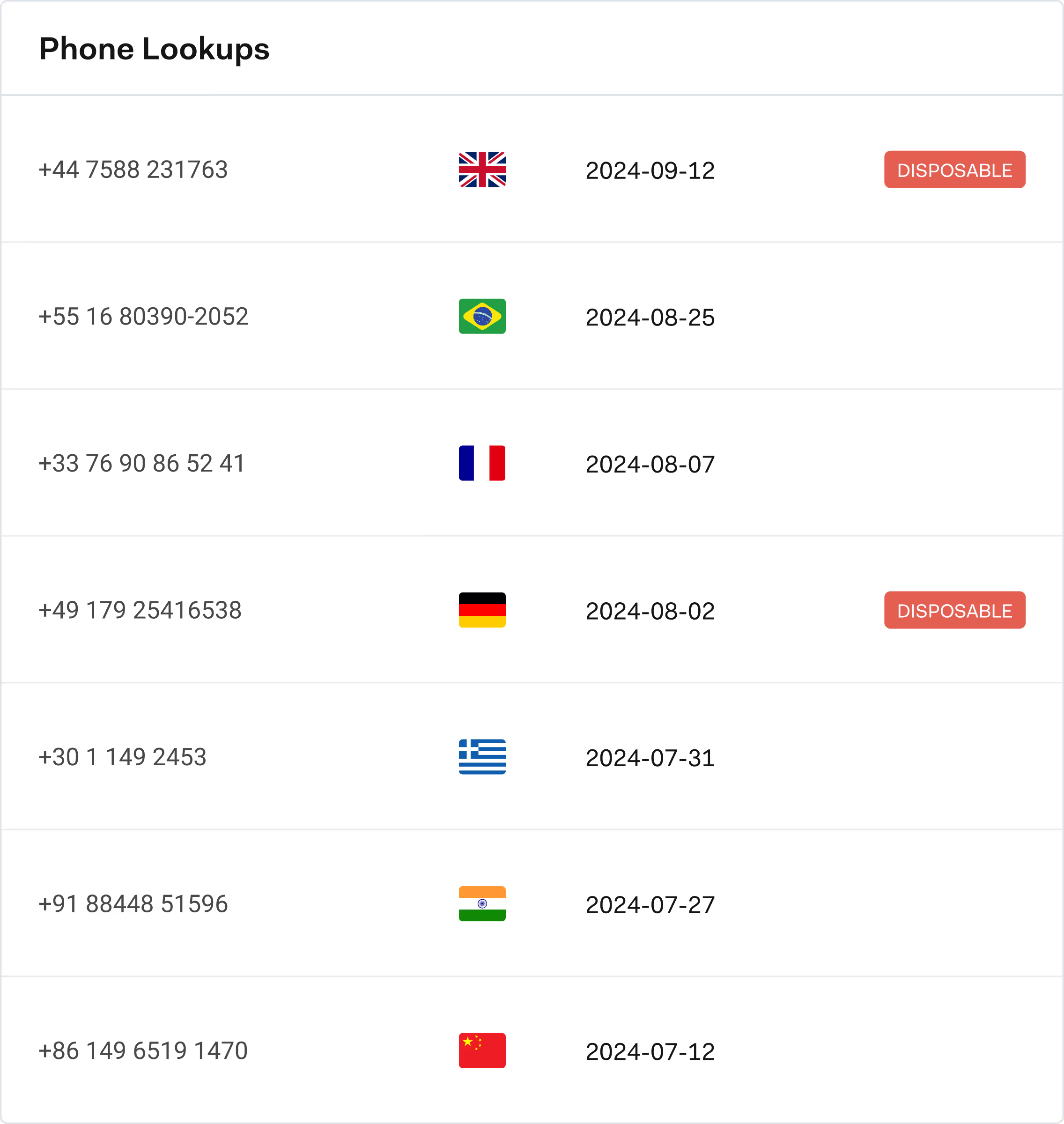
Common red flags include many referrals coming from the same IP, device or location, a high number of new users sharing similar contact details, and short-lived accounts that redeem a promo and quickly churn. You may also see spikes in referrals right after a campaign launch from unusual geographies, or abnormal patterns where one referrer generates an unrealistic number of “friends” in a short period.
Fraudsters combine breached or stolen personal data with fabricated identities, disposable emails and virtual phone numbers. They use scripts, emulators and device farms to create and manage large volumes of accounts that appear distinct on the surface. These accounts sign up through referral links, redeem welcome offers and apply promo codes repeatedly, often cashing out bonuses, reselling discounted goods, or converting rewards into money or crypto.
Effective strategies include analyzing emails and phone numbers, using device and IP intelligence, and linking referrers and referees through OSINT-based checks. Layering data sources, such as phone-to-name, email-to-name and IP clustering, helps flag risky referrals in real time while genuine customers enjoy a smooth, low-friction experience.
Learn more about Referral & Promo Abuse
Protect your business from promo abuse with Trustfull











