Payment fraud
Verify payees before money leaves the account
Payment fraud at a glance
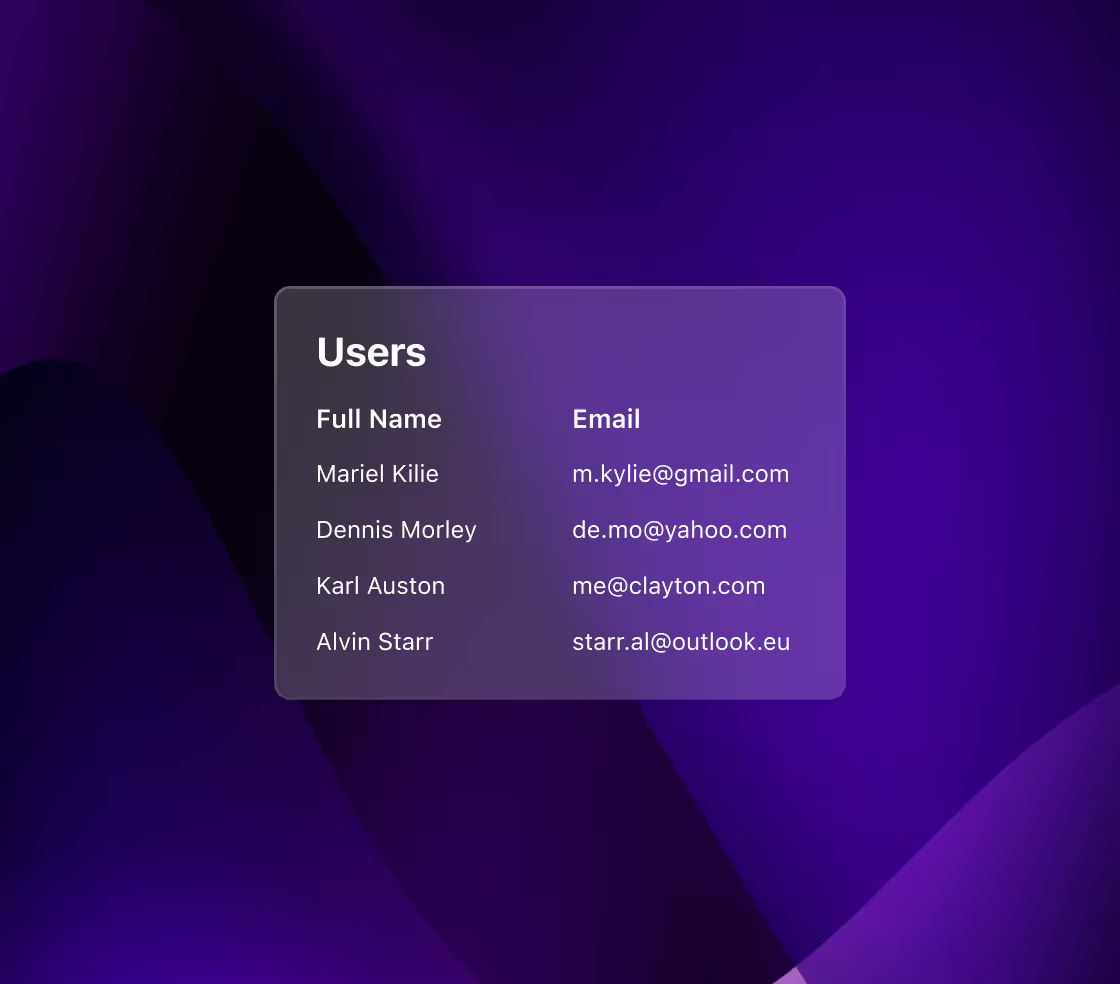


Payment protection without added friction
Real-time defence
Assess payer and payee risk in real time at login, checkout or beneficiary creation.
Silent checks
Run background checks to block fraudulent transactions without getting in the way of legitimate ones.
Powered by OSINT
Leverage the power of hundreds of open source intelligence signals to spot inconsistencies and red flags.
Flexible Rules
Customize scoring models and risk rules for different channels, use cases and regulatory environments.
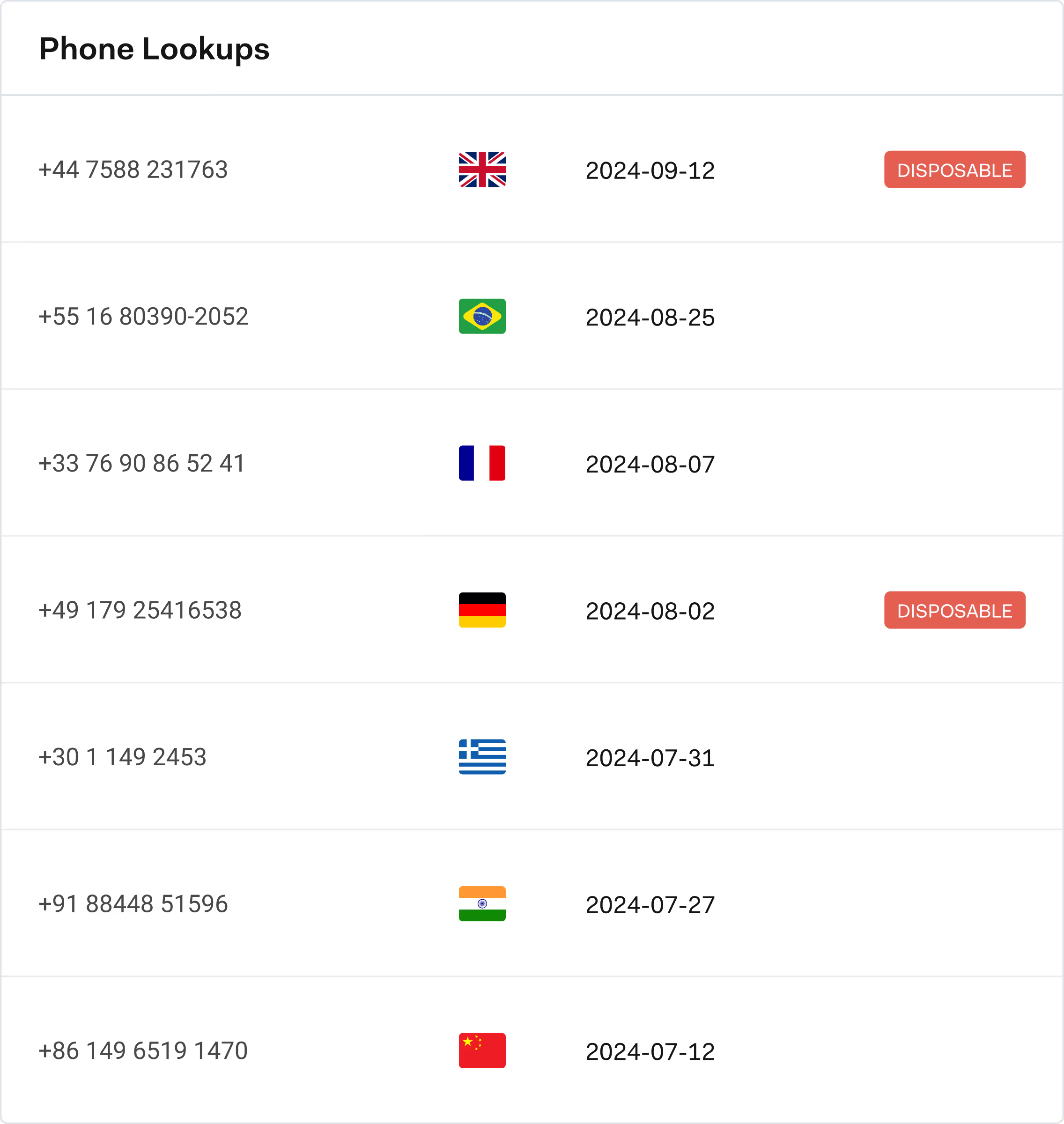
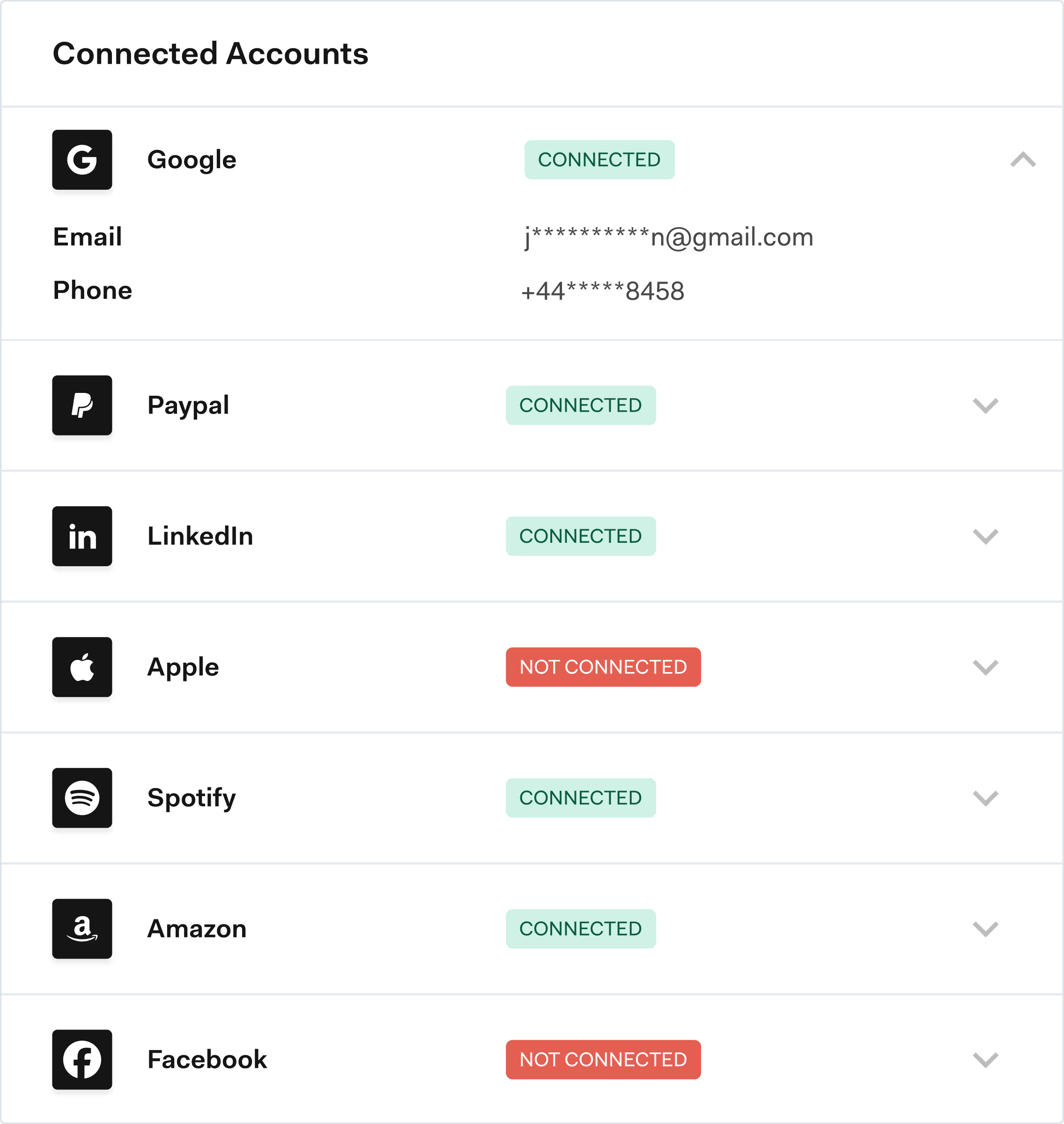
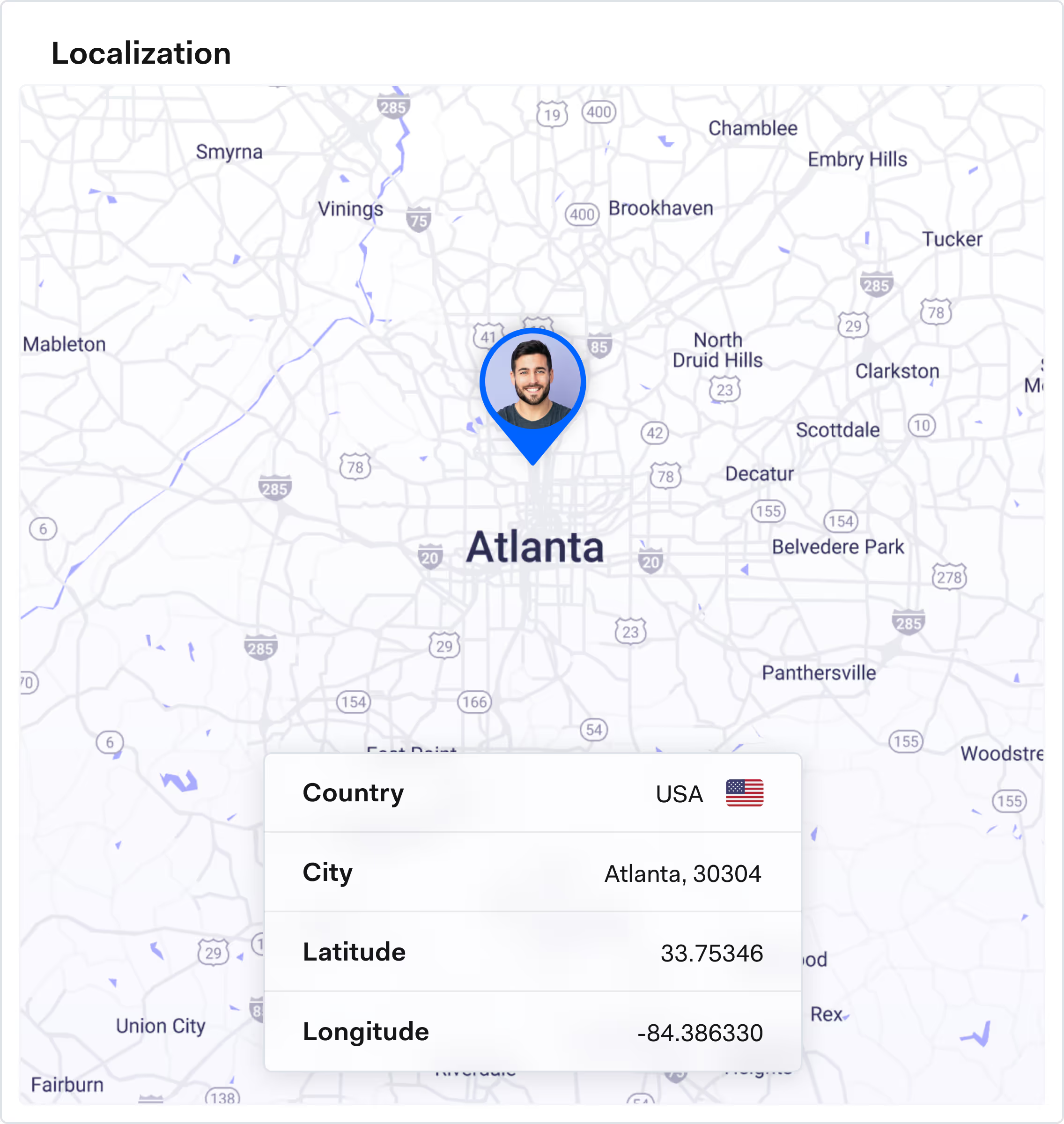

Frequently asked questions
Key types include authorised push payment / beneficiary impersonation scams, account takeover-based payments and withdrawals, card-not-present fraud, card testing and small probes at scale,. These patterns often overlap, with the same actors using stolen data, social engineering and mule accounts to move funds.
Red flags include new beneficiaries with urgent, high-value requests; sudden changes to account or payee details; multiple declined attempts followed by a successful transaction; unusual ticket sizes; and repeated use of different cards or accounts from the same device or IP.
Fraudsters rely on phishing kits, spoofed domains and social engineering scripts to launch scams at scale. At the same time, they use credential stuffing tools, bots and automation to test huge volumes of stolen cards and logins with micro-transactions.
Phone and email analytics, IP and device intelligence, OSINT-based checks and real-time risk scoring allow organisations to step up controls only when risk is high, while trusted customers continue to process transactions with minimal disruption.
Learn more about Payment Fraud
Protect your business from payment fraud with Trustfull










