Account takeover
Prevent unauthorized access in real time
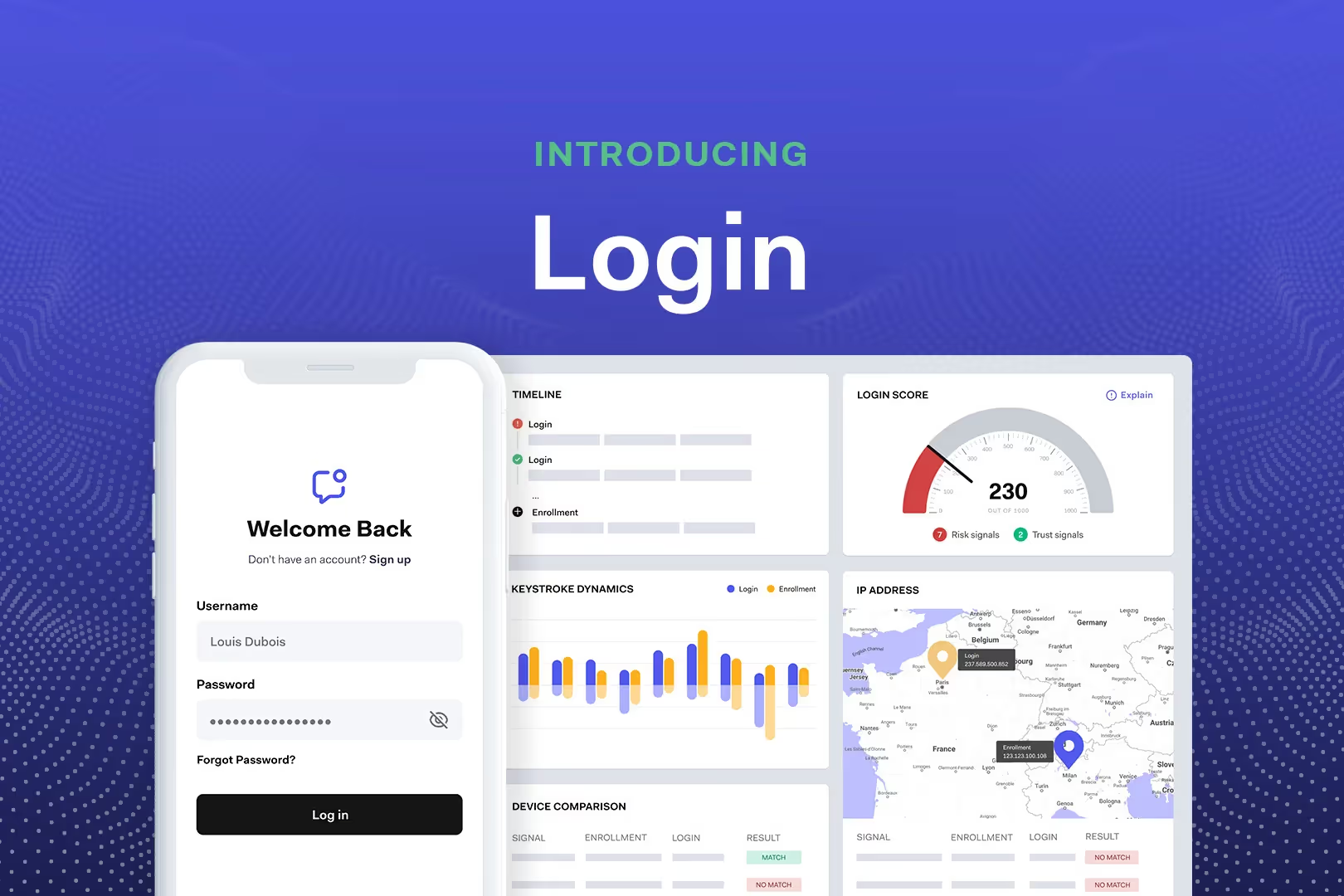
Account takeover at a glance

Prevent ATO attacks with silent checks
Biometrical
Analyze unique typing patterns and browser behavior to authenticate users accurately.
Self-Learning
Leverage dynamic authentication that grows smarter with each user sign-in.
Lightweight
Handle both enrollments and verifications with a single, easy-to-use endpoint.
Frictionless
Ensure a seamless login experience with fully silent authentication.
Frequently asked questions
Account takeover fraud is when a criminal gains unauthorized access to a genuine customer account and uses it for theft or abuse. Fraudsters typically obtain login credentials via data breaches, phishing or malware. Once inside, they change details, lock out the real user, and cash out.
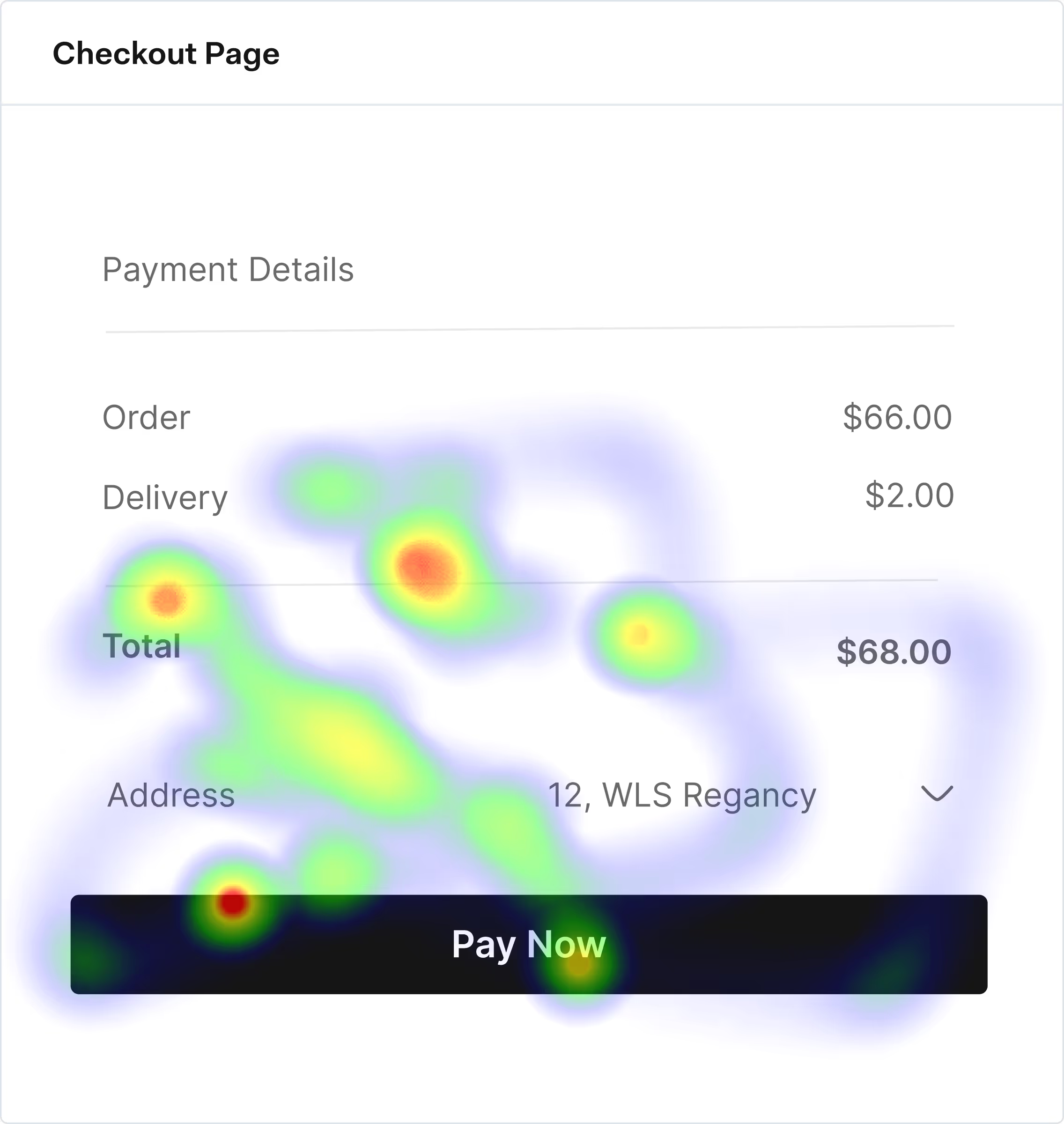
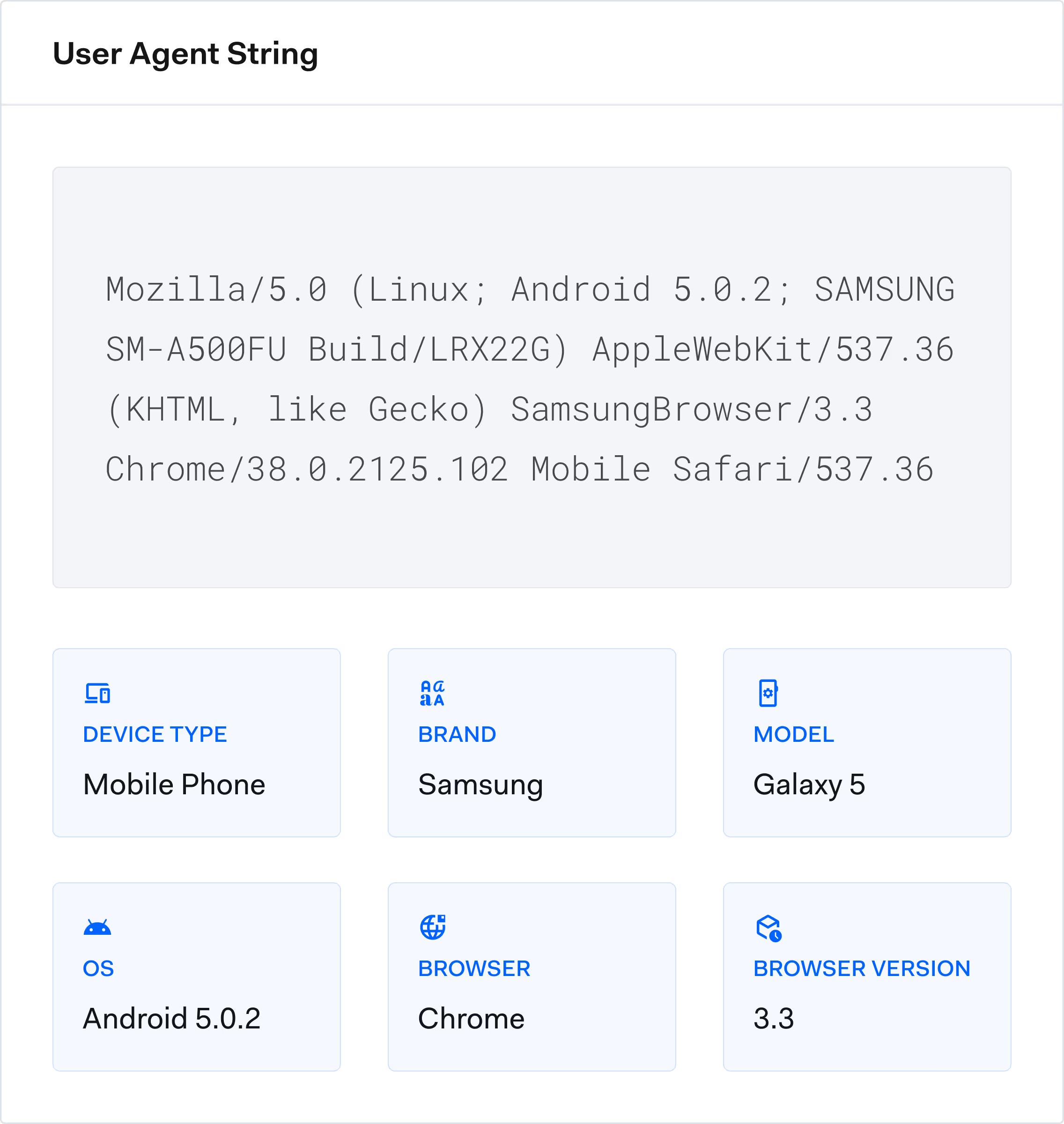
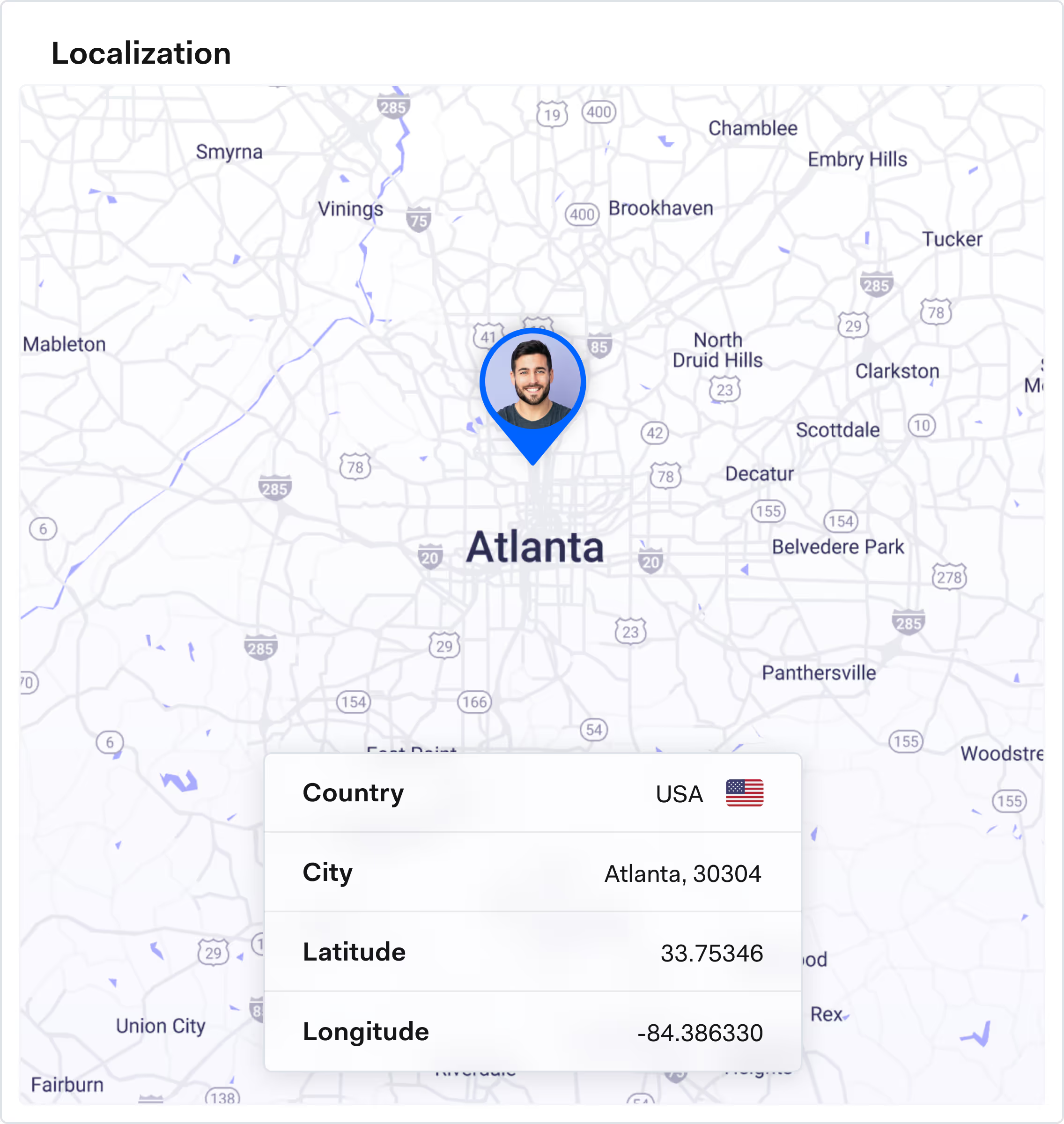
Key signs of ATO include sudden password, email, or address changes and logins from unusual devices, locations, or IPs. You may see high-value orders, new payees added, or multiple failed login attempts followed by a successful one.
Fraudsters use phishing emails, fake websites, and social engineering to trick users into revealing credentials. They also buy leaked passwords from data breaches, deploy malware or keyloggers, and run credential stuffing using reused passwords. Weak, reused, or shared credentials make attacks much easier.
Businesses can deploy risk-based authentication that steps up checks only on suspicious logins or actions. Using device and IP intelligence, behavioral analytics, and login velocity checks to spot anomalies is also a common and very effective strategy. Finally MFA, strong password policies, and alerts for key account changes are all methods to secure authentication while keeping friction in check for low-risk flows.
Immediately secure the affected accounts by forcing password resets, revoking active sessions, and validating recent changes. Review and reverse fraudulent transactions where possible and notify impacted customers with clear next steps. Finally, investigate the root cause, tighten controls, and update monitoring rules to prevent repeat attacks.
Learn more about Account Takeover
Protect against account takeover with Trustfull