Article
What Is Risk Scoring and How Does It Work?
Uros Pavlovic
June 27, 2024

Risk scoring plays a key role in today’s financial and fintech industries, where fast change and high stakes are the norm. It harnesses the power of alternative data - trust & risk signals derived from phone numbers and email addresses as well as IP and device data - to detect and evaluate the potential risks posed by each digital interaction, ensuring that security measures are both dynamic and informed.
In this blog post, we explore the specific mechanics of risk scoring, detailing how it transforms raw data into a nuanced predictive tool to identify and stop fraudulent activities before they can cause harm.
What is risk scoring?
At its heart, risk scoring is the systematic analysis of various risk factors associated with an individual's or entity's actions within a system, aimed at predicting the likelihood of fraudulent outcomes. The process begins with the collection of digital footprints captured through interactions with digital platforms.
This collected data, often termed alternative data, offers a deeper insight into the user’s digital behavior, allowing financial institutions to move beyond traditional credit scores and demographic data. The essence of risk scoring lies in its ability to transform this data into actionable intelligence. By employing sophisticated algorithms, risk scoring evaluates each interaction's risk level, assigning scores ranging from low to high risk. These scores are crucial for financial organizations as they navigate through the challenges of approving transactions, onboarding new customers, and maintaining secure operations.
But why is there a need for calculating risk scores anyway? The simple reason is that modern-day fraudsters are improving their methods of illicit activities. In addition, the last few years have seen a jump in deepfake fraud activities, during which Britain alone lost £580 to fraud (that’s according to FT). Read more about Emerging Identity Scams and Fraud Trends in 2025.
These trends are getting more serious every year, which is why financial organizations are investing more in fraud and risk scoring to help them clearly identify which users, transactions or interactions pose a greater risk to their business. As a framework, risk scoring doesn't aim to only uncover fraudsters, but also to enhance user experience and minimize friction for legitimate users. In environments where speed and security are key, such as in banking, online lending, or cryptocurrency exchanges, a well-calibrated risk scoring system can differentiate between a potential threat and a genuine customer swiftly and accurately.
In the following sections, we will delve deeper into the mechanisms of risk intelligence, explore how it leverages digital signals to establish patterns of risk and trust, and look at practical applications in silent checks and pre-KYC methods to fortify fraud prevention strategies.
The mechanics of risk intelligence
Risk intelligence forms the backbone of effective risk scoring systems. It capitalizes on the wealth of data that digital interactions provide, using it to differentiate between normal customer behavior and potential fraud. The process starts with the collection of digital signals—data points like phone numbers, email addresses, IP addresses, browser details, and device configurations—that individuals leave behind as they navigate through digital spaces.
Analysis of digital signals
The first step in deploying risk intelligence is the detailed analysis of these digital signals. By examining data such as the geolocation linked to an IP address, the device type, or even the operating system, risk analysts can create a baseline of expected behavior for each user. This baseline is crucial, as it helps identify deviations that might suggest fraudulent activity.
For instance, if a user typically accesses a service from a specific IP range and suddenly switches to a vastly different geographic location, this could raise a red flag. Similarly, a sudden change in device type or browser version might indicate that a different person has gained access to the user's credentials.
Establishing patterns of risk and trust
Using machine learning algorithms, risk scoring models are trained to recognize patterns of both risk and trust. These models are continuously updated with new data, improving their accuracy over time. They can distinguish between a wide array of behaviors, categorizing them into risk levels. For example, a transaction that matches the usual pattern of a user’s behavior may receive a low-risk score, while an anomaly in their purchasing behavior could be flagged as high-risk.
This nuanced understanding allows organizations to apply what's known as "silent onboarding" and "silent checks." These methods assess risk without interrupting the user experience, maintaining the delicate balance between security and customer satisfaction. Silent onboarding, in particular, is a critical strategy during the customer acquisition phase, where the potential for fraud is high, but so is the need for a smooth user experience to ensure customer conversion.
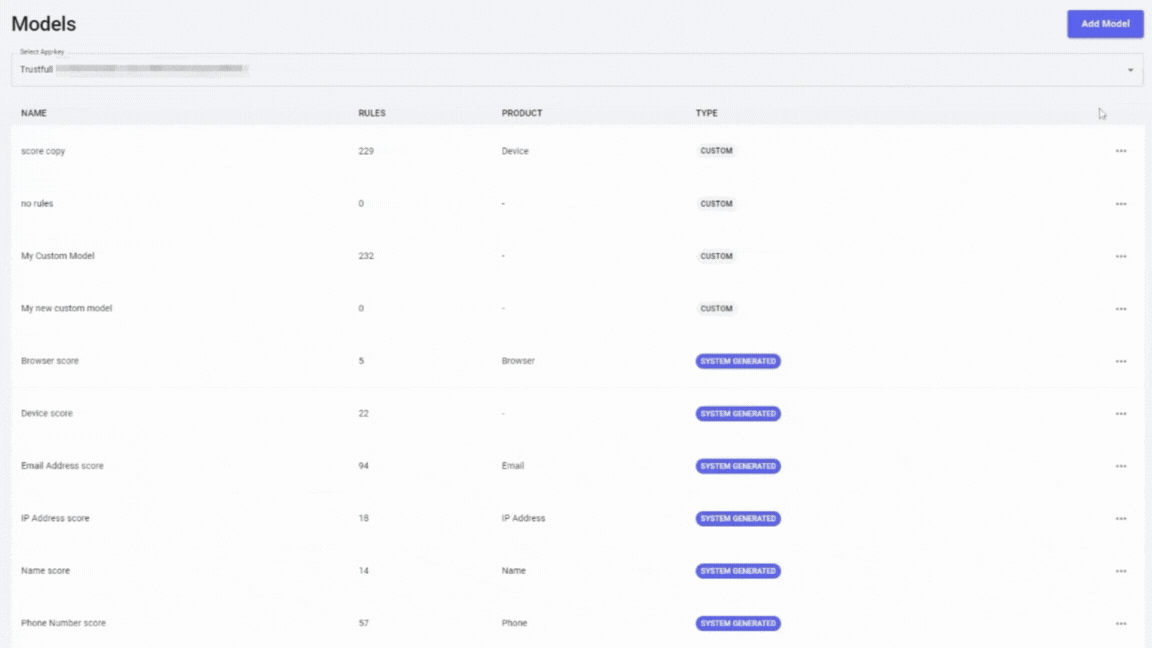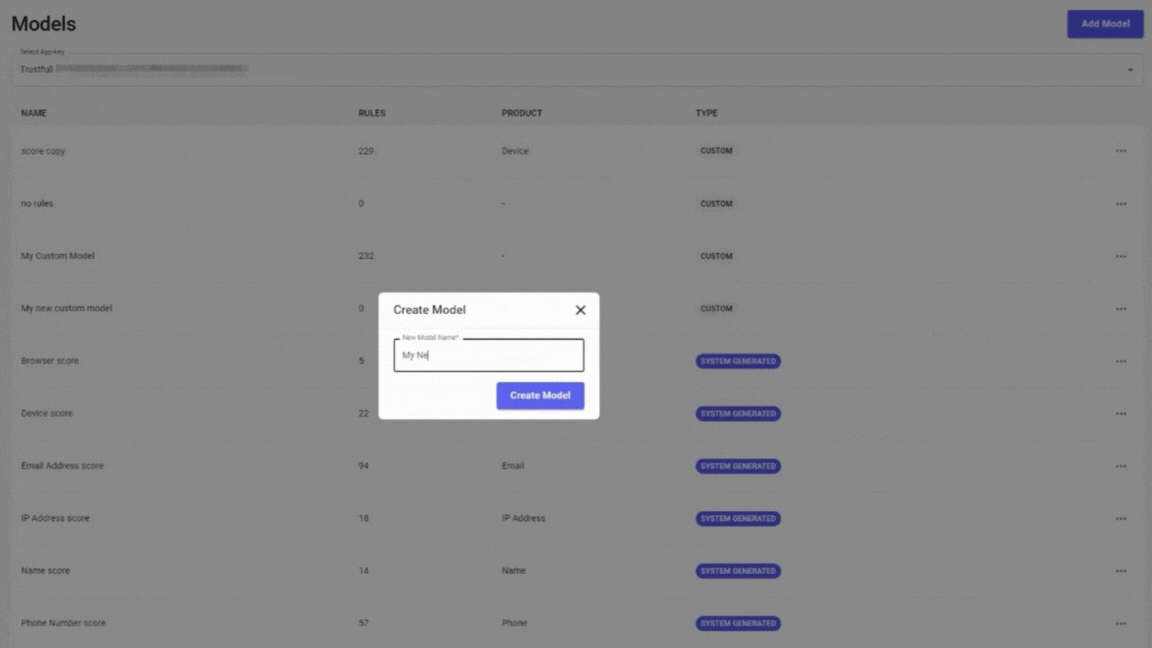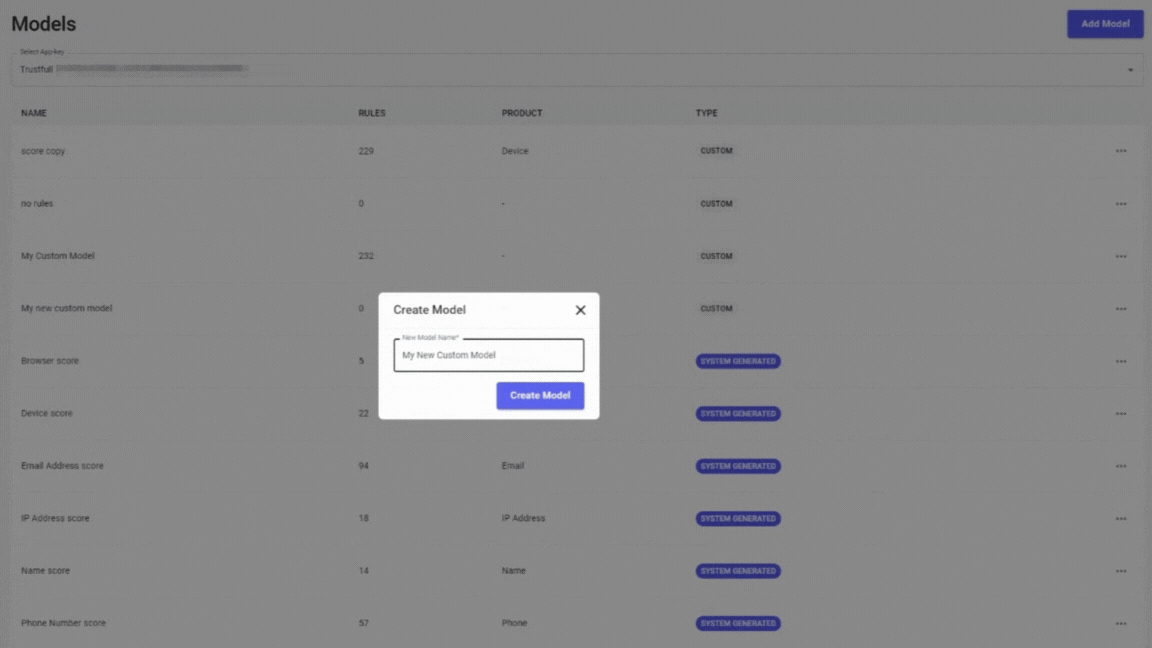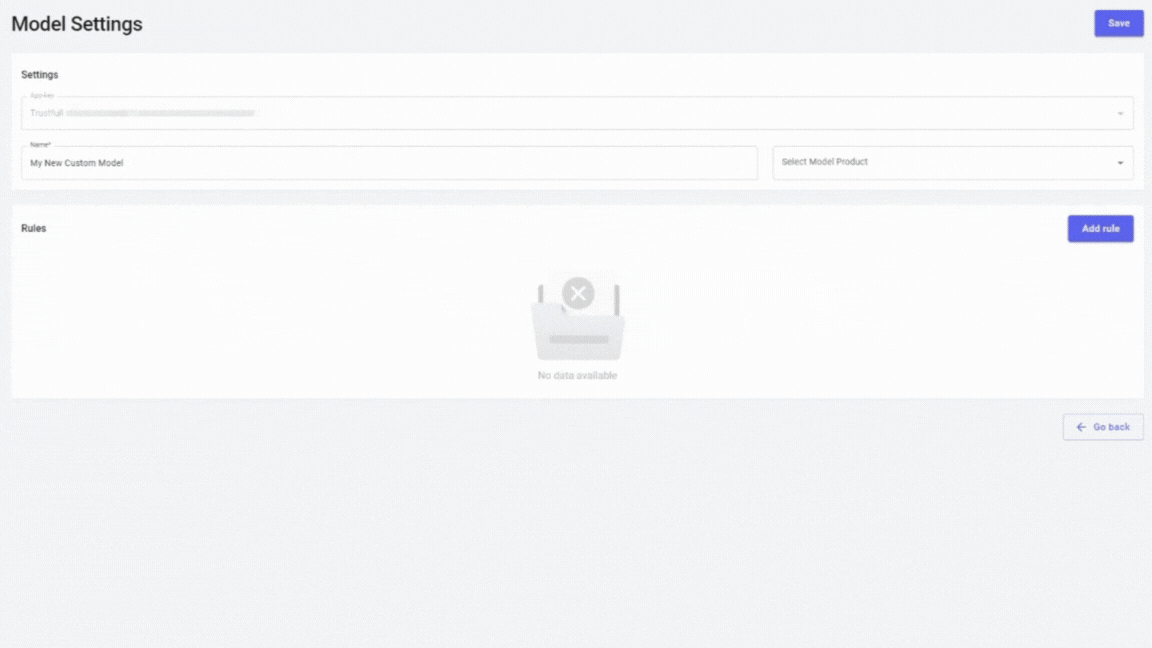
Custom and preset risk scoring models
Risk intelligence platforms enable the creation of both custom and preset risk scoring models. Preset models offer a turnkey solution, designed based on industry-wide data and common fraud scenarios, which can be deployed quickly and efficiently. Custom models, on the other hand, are tailored to the specific needs of an organization. They take into account unique aspects of the business model, customer base, and typical transaction types.
These models are not static; they evolve based on ongoing analysis and feedback. As new types of fraud emerge, and as customer behavior changes, the models adapt, ensuring that they continue to offer robust protection against fraud.
Silent checks and pre-KYC: tools for early fraud detection
In the landscape of digital finance, early detection of potential fraud is crucial. Silent checks and pre-KYC (Know Your Customer) methods are sophisticated tools that play a pivotal role in identifying and mitigating risks before they escalate into actual fraud. These methodologies leverage the foundational elements of risk scoring to secure onboarding processes and ongoing transactions without disrupting the user experience.
Silent checks: seamless security
Silent checks are conducted in the background during user interactions, such as account creation or during transactions. This method utilizes the risk scoring models to assess the risk associated with a user’s activity in real-time, without the user being aware that a check is occurring. For instance, when a new user registers on a platform, the system automatically analyzes the submitted data—like email, phone number, and device details—against known risk indicators.
The advantage of silent checks lies in their ability to maintain a frictionless user experience. By minimizing disruptions, businesses can enhance customer satisfaction while still adhering to high-security standards. Silent checks are especially valuable in environments where speed and efficiency are paramount, such as in online marketplaces or during flash sales on e-commerce platforms.
Pre-KYC methods: effective risk management
Pre-KYC methods are an extension of silent checks, where additional data points are gathered and analyzed before a full KYC verification process is initiated. This approach allows financial institutions and fintech companies to filter out potential risks at an early stage, thereby reducing the cost and time involved in handling high-risk customers later on.
By employing pre-KYC checks, companies can detect discrepancies or anomalous patterns that might suggest identity theft, synthetic identities, or other forms of financial fraud. For example, matching the submitted contact details against global databases or checking for the presence of the email or phone number in previous fraud reports can provide early warnings of potential fraud.
Integrating silent checks and pre-KYC into risk management strategies
Integrating these tools into the broader risk management strategy enhances overall fraud prevention efforts. Financial organizations can tailor their approach based on the risk levels assigned during these checks, deciding on the depth of KYC needed or the immediacy of further verification processes. This tiered approach to security allows companies to allocate resources more efficiently, focusing intensive verification efforts on higher-risk scenarios while streamlining approvals for low-risk interactions.
In the next section, we'll explore how these technologies can be customized for different industries, enhancing their effectiveness and ensuring that each sector's unique risks are addressed appropriately.
Customizing risk scoring models for diverse industries
The adaptability of risk scoring models to diverse industries is crucial for addressing the unique challenges and threats each sector faces. From banking to online marketplaces, each industry has distinct risk profiles and customer behavior patterns that require tailored risk management strategies.
Banking & neobanks
In the banking sector, particularly with neobanks that operate primarily online, risk scoring must be exceptionally dynamic to cope with the rapid digital transactions and the variety of threats, from identity theft to account takeover. Custom risk models for these institutions focus on detecting unusual transaction patterns and verifying customer identities without adding unnecessary friction to the customer experience.
Online lending
For online lenders, risk scoring is pivotal in assessing the creditworthiness and fraud risk of applicants quickly and accurately. These models assess everything from application inconsistencies to historical financial behavior, providing a comprehensive risk profile that helps lenders make informed decisions about loan approvals.
Insurance
In the insurance industry, risk scoring models help in identifying potential claim frauds and evaluating the insurance risks based on historical data and behavioral patterns. These models are crucial for maintaining profitability while ensuring that claims are processed quickly and fairly. One of the key use cases in this industry is underwriting fraud, and many online insurance companies are looking for ways to tackle this problem.
Payment providers
Payment providers use risk scoring to prevent transaction fraud by analyzing transaction patterns and flagging anomalies that could indicate fraud, such as unusual purchase sizes or frequencies. Their models are designed to operate in real-time, providing immediate assessments to prevent fraudulent transactions while minimizing false positives that could disrupt legitimate transactions.
Betting and iGaming
For the betting and iGaming industry, risk scoring models focus on behaviors indicative of money laundering or the use of stolen financial information. These models need to adapt quickly to changes in user behavior and new fraud techniques to protect both the business and its customers.
Cryptocurrency
The cryptocurrency sector faces unique challenges due to its anonymity and the fluidity of transactions. Risk scoring models here are geared towards identifying patterns indicative of money laundering, wallet theft, and other crypto-specific frauds.
Online marketplaces
Lastly, online marketplaces must manage a broad spectrum of fraud risks, from fake listings to buyer and seller scams. Risk scoring models in these environments focus on transaction security, user verification, and pattern recognition to prevent fraud while facilitating a trustworthy marketplace environment.
Industry-specific customization benefits
Customizing risk scoring models for these specific industries not only enhances their effectiveness but also ensures that fraud prevention strategies are as seamless as possible for genuine customers. By tailoring models to industry-specific needs, organizations can better protect themselves and their customers from emerging threats, all while maintaining a competitive edge in the fast-paced digital economy.
The risk scoring process: step-by-step
Understanding the step-by-step process of risk scoring is essential for appreciating how comprehensive fraud prevention mechanisms operate. This detailed breakdown reveals how data is transformed into actionable insights that protect businesses and their customers.
- User action initiation: the process begins when a user initiates an action, such as logging in, making a transaction, or registering a new account. This action triggers the risk scoring system to start evaluating the activity.
- Examination of user data: the system examines the data provided by the user, such as phone numbers, email addresses, and more. It also gathers additional data from the user's device, like IP addresses and device configuration. This comprehensive data collection is crucial for a full understanding of the context of the user's action.
- Data enrichment: following data collection, the risk scoring system enhances the gathered information through data enrichment processes. This might involve cross-referencing information against external databases to verify identity and check for any past involvement in fraudulent activities.
- Data analysis by a risk intelligence platform: the enriched data is then fed into the risk intelligence platform. Here, advanced algorithms analyze the data to detect any discrepancies or patterns indicative of fraudulent behavior.
- Application of fraud rules: based on the analysis, the system applies predefined fraud rules, which can assign positive or negative scores to various aspects of the data. These rules are designed to flag high-risk behaviors and separate them from normal activities.
- Calculation and interpretation of the final risk score: After applying the fraud rules, the system calculates the final risk score, providing a detailed explanation of the reasoning behind the score. This score determines the risk level associated with the user's action.
- Predefined actions based on risk categorization: depending on the resulting risk score, predefined actions are applied:
- Good (Trustworthy): The action proceeds without any additional checks.
- Moderate (Slightly Risky): The action may require additional verification.
- Bad (Risky)
- Poor (Very Risky): The action is blocked or flagged for manual review.
This structured process ensures that each user action is assessed accurately, maintaining security while optimizing the user experience.
Advanced techniques in fraud prevention
To further enhance the effectiveness of risk scoring models, advanced techniques such as AI-powered image analysis are increasingly being integrated into the fraud prevention arsenal.
AI-Powered image analysis
One of the most innovative additions to risk scoring is AI-powered image analysis. This technology involves several key steps:
- Face match: automatically retrieves faces from any photos linked to an email address or phone number, ensuring that the images are relevant to the user's profile.
- Comparison algorithm: utilizes advanced algorithms to analyze the extracted faces, calculating a similarity percentage that reflects how closely the images match.
- Anomaly detection: the system identifies any deviations or inconsistencies in facial features, which could indicate potential synthetic identities or manipulated documents.
- Fraud prevention: By detecting these anomalies early, the system acts as a robust barrier against identity fraud, significantly enhancing the security of digital interactions.
Utilizing the rule engine
Another critical tool is the rule engine, or model builder, which allows organizations to create bespoke risk models that align with their specific risk policies and sensitivity levels. This customization is vital for adapting to new fraud trends and ensuring that fraud prevention strategies remain effective.
By leveraging these advanced techniques, organizations can significantly strengthen their fraud prevention frameworks, reducing the incidence of fraud and building trust with their customers.
What's next for risk scoring
As we look toward the future of risk scoring in fraud prevention, it's essential to consider the upcoming features and innovations that could redefine how businesses approach security and risk management. While maintaining subtlety about their implementation, here are some key developments on the horizon that promise to enhance the capabilities of risk scoring systems.
Transaction enhancements
One of the most anticipated advancements is in the realm of transaction monitoring. Future iterations of risk scoring systems are expected to incorporate more dynamic and comprehensive monitoring techniques. These enhancements aim to analyze transaction patterns in real-time, identifying anomalies that could indicate fraudulent activities such as money laundering or unauthorized fund transfers. By integrating more complex algorithms and learning capabilities, these systems will not only detect fraud more effectively but also reduce false positives, thereby improving the customer experience.
Another significant area of development is in chargeback fraud prevention. As e-commerce continues to grow, so does the challenge of dealing with chargebacks initiated under fraudulent circumstances. Upcoming risk scoring models are looking to integrate predictive analytics that can preemptively identify transactions at high risk for chargebacks. This proactive approach allows businesses to address disputes before they escalate, potentially saving significant amounts of money and reducing the impact on operational resources.
Integration with new tech
The integration of emerging technologies such as blockchain and biometrics will further refine risk scoring systems. Blockchain offers a new layer of security by providing immutable transaction records, making it harder for fraudsters to manipulate data. Simultaneously, biometric verification technologies like facial recognition and fingerprint scanning are becoming more sophisticated, offering additional layers of security that can be incorporated into the risk scoring process.
Adapting to new regulatory requirements
As regulatory landscapes evolve, risk scoring systems must adapt to comply with new legal standards and privacy regulations. This adaptation will likely include enhancements in data protection and privacy measures, ensuring that risk scoring practices remain transparent and within legal boundaries.
Customizable AI models
Finally, the development of more customizable AI models will allow businesses to tailor their risk scoring systems more precisely to their specific needs. These models will be able to learn from a broader range of data inputs, adapting over time to new fraud tactics and evolving industry trends.
Creating customized risk scoring with Trustfull
Risk scoring is more than just a protective measure; it's a crucial element of modern business operations that enhances both security and customer trust. Creating customized risk scoring by utilizing the Trusfull API to score millions of customer interactions to identify potential risks or opportunities can be the first step to a more streamlined fraud prevention strategy.
To discover more about this, please reach out to our team of fraud experts who can help you improve your financial security, thus putting a stop to new account fraud, synthetic identity fraud, money muling, and so on.



