Account sharing
Spot shared logins and subscription abuse
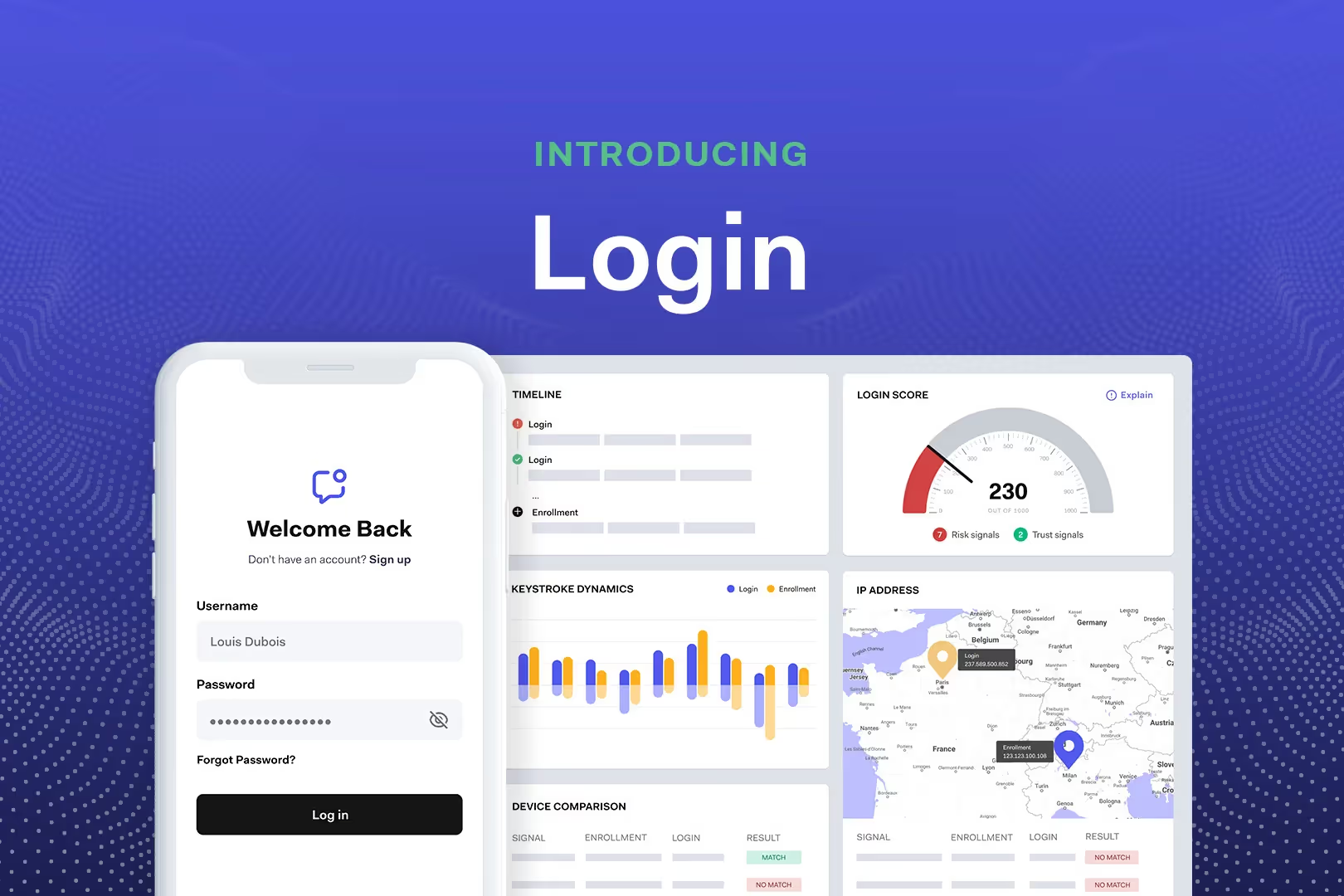
Account sharing at a glance
Silent protection against account sharing
Abuse detection
Identify suspicious behavior and stop password-sharing attempts.
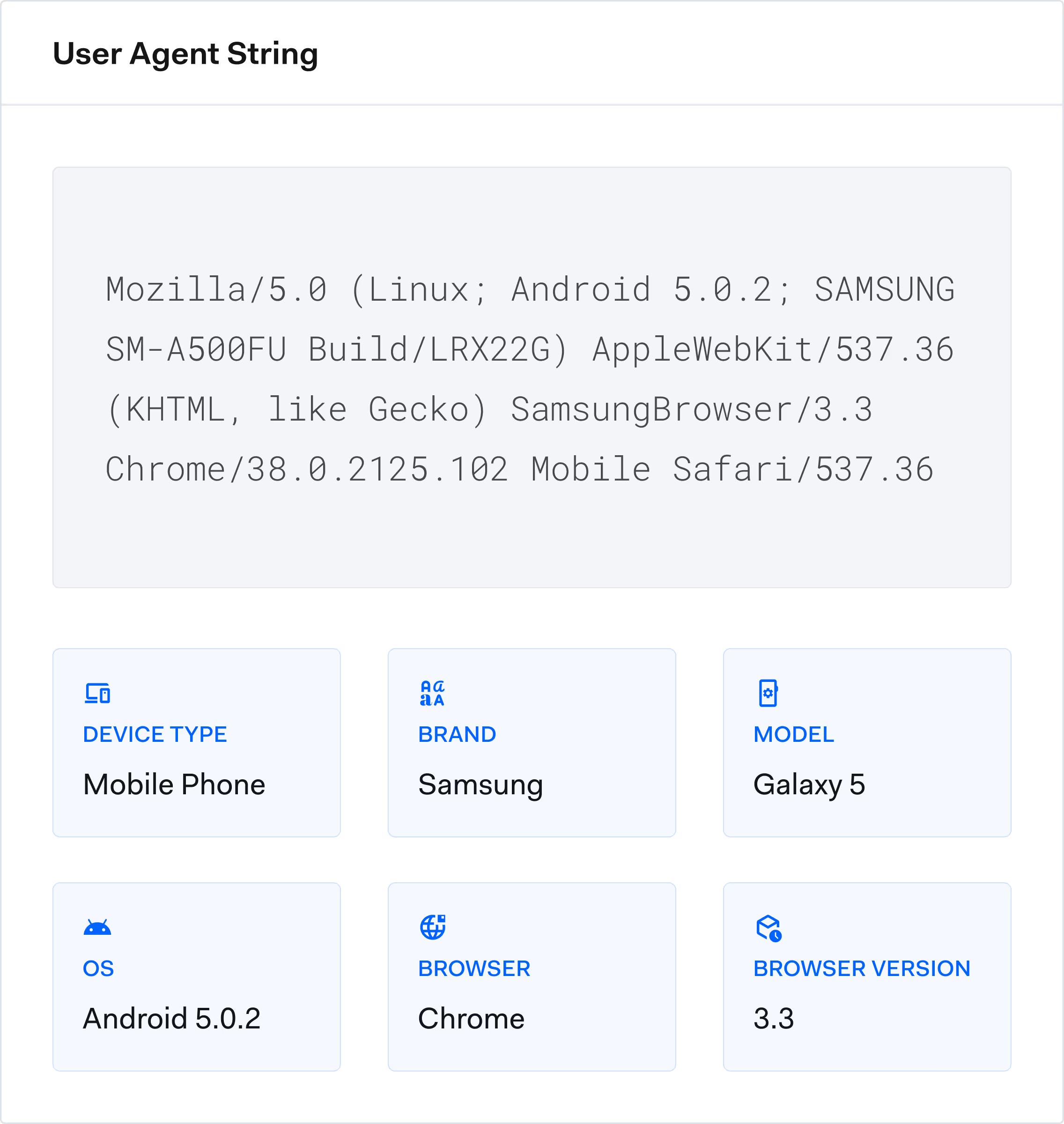
Real-time signals
Hundreds of digital signals for instant account-sharing detection.
Silent protection
Our checks run in the background, with no impact on the UX.
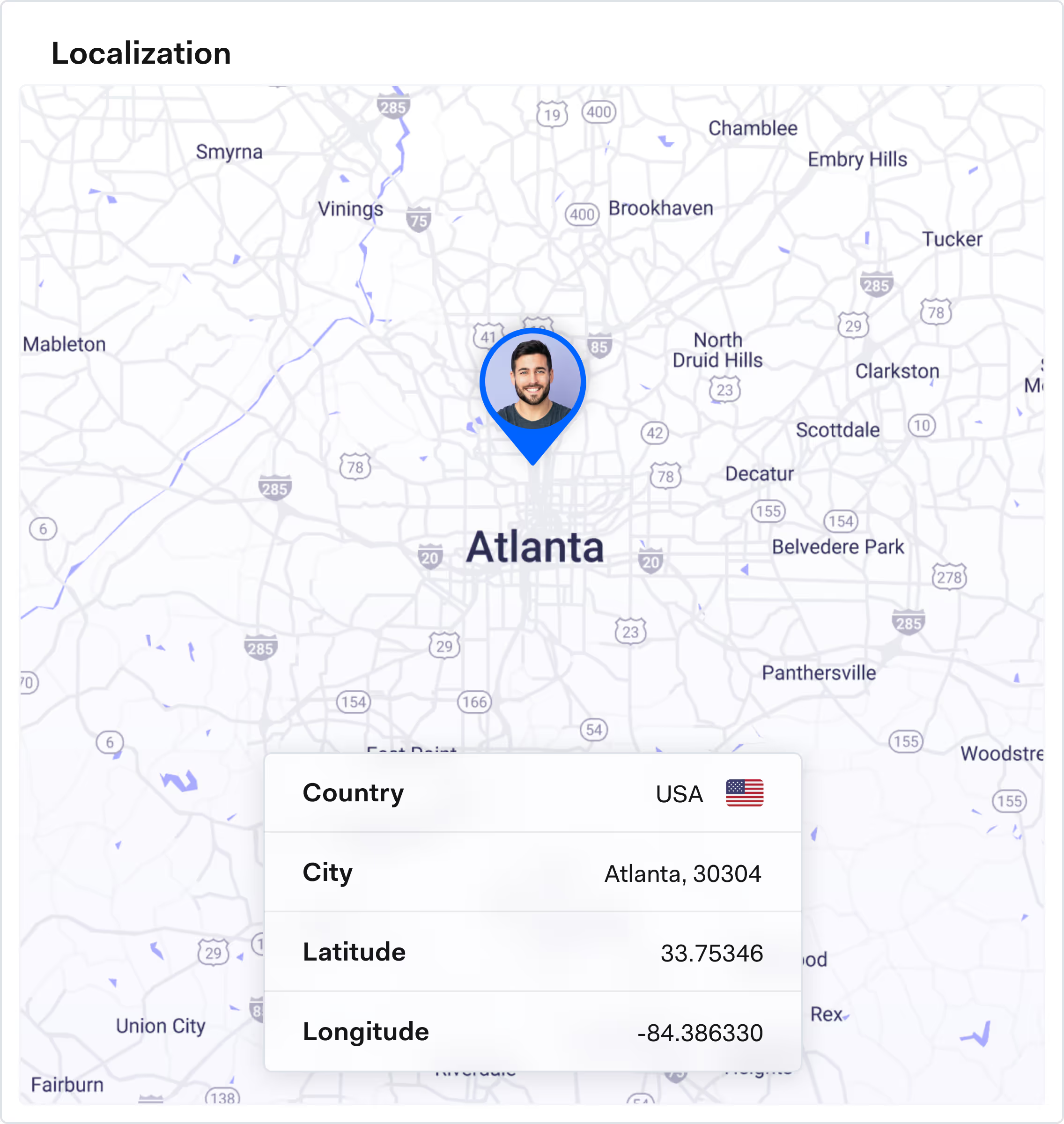
Global coverage
Reliable account-sharing coverage, no matter where your users are.
Frequently asked questions
Account sharing happens when multiple people use the same set of credentials to access a service that is priced or licensed per user, device or household. In more severe cases, credentials are resold or “rented out” at scale, allowing many unauthorized users to piggyback on a single paid subscription or license.
Benign sharing might involve light usage between close family members or occasional multi-device access by a single user, depending on the terms of service. Abusive behaviour includes systematic sharing outside allowed policies, credential reselling, or using one account to support entire organisations or communities, significantly undermining revenue and fair-use limits.
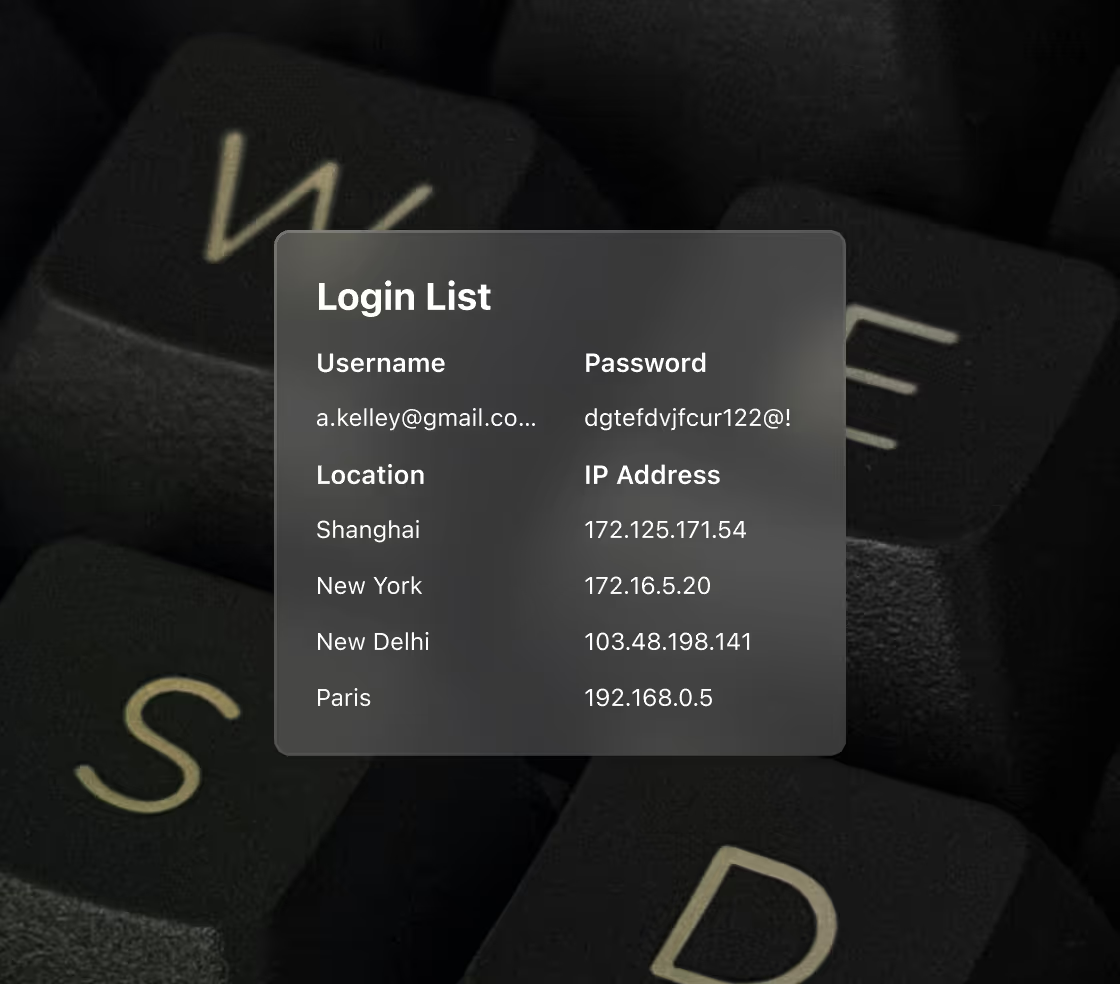
Typical red flags include logins from multiple locations within short timeframes, many devices or browsers tied to a single account, and unusual patterns such as very high concurrent usage or access from shared corporate networks on a consumer plan.
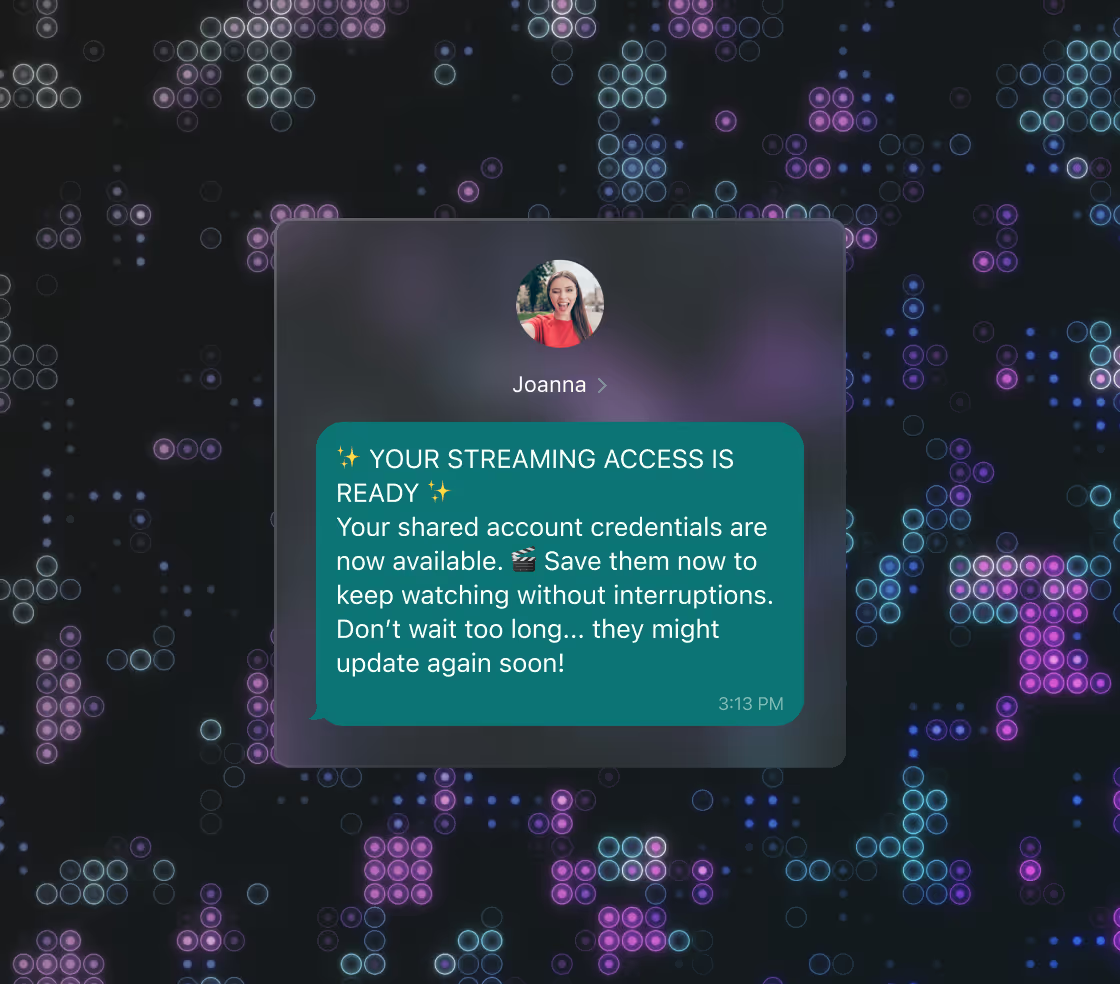
Fraudsters may buy discounted subscriptions or take advantage of promotions, then resell access through social media, forums or dedicated “account shops.” In parallel, stolen credentials from data breaches can be tested via credential stuffing tools, with successful logins resold or bundled into “premium accounts” shared by many unauthorized users.
Effective strategies combine device, browser and IP intelligence with behavioural analysis and OSINT-based checks. By scoring risk in real time and only challenging or blocking suspicious sessions, companies can preserve a smooth login experience for genuine users while enforcing fair-use policies, tier limits and regional restrictions.
Learn more about Account Sharing
Fight back against account sharing with Trustfull