Article
How to Spot Money Mule Red Flags in Banking
Uros Pavlovic
February 6, 2024

In today’s banking sector, financial transactions are constantly under scrutiny. Among the numerous challenges banks and neobanks face, identifying money mule red flags emerges as a pivotal aspect of fincrime prevention. Money mules, often unaware accomplices in broader financial crimes, can be the linchpin in the laundering of illicit funds, making their detection not just a matter of regulatory compliance, but a cornerstone of ethical banking practices. This article delves into the nuanced world of money mule red flags, offering insights into the patterns and behaviors that signal such activities, and reinforcing the need for vigilant and informed action in the banking sector.
How does mule account creation work?

Money muling isn’t a problem affecting only one region. For quite some time, money mules have been targeting financial institutions across Europe, Asia, and the Americas. For instance, 19,000 money mules were investigated in Singapore in the period 2020-2023.
But how does money muling work? What are its main signs?
To effectively spot money mule red flags, it’s essential to first understand how mule accounts are created. Fraudsters involved in fincrime activities usually use two types of methods to establish mule accounts:
- New account opening approach: fraudsters employ stolen personal information or synthetic identities to initiate the creation of new accounts, thereby making it hard for financial institutions to trace them directly. Following the creation of these accounts, perpetrators often adopt a dormant approach, allowing the accounts to remain inactive for a period to avoid arousing suspicion from banks. At a later stage, these dormant accounts are used to cash out and launder funds transferred from compromised accounts. Notably, criminals may exploit various avenues, such as marketing programs or promotional initiatives to drive customer acquisition, to facilitate the opening of new accounts. A contemporary trend involves the exploitation of vulnerabilities within the account opening process through the use of bot-generated variations, allowing for the systematic and large-scale initiation of mule accounts.
- Mule recruitment tactics: while money laundering has historical roots, contemporary criminals have adopted various innovative methods to expand the pool of individuals serving as money mules within the system. This diverse group of mules includes those who are consciously participating (witting money mules), those who choose to remain oblivious to the nature of their involvement (willfully blind money mules), and those who are entirely unaware of their complicity (unwitting money mules). The digital landscape has significantly facilitated the creation of extensive networks for money mule schemes, exacerbating the issue in recent years. Criminals leverage the speed, efficiency and anonymity of digital channels to establish and maintain these networks, further impeding efforts to curtail the proliferation of money mule activities.
Spotting common money mule red flags
Money muling is fraught with indicators that, if correctly identified, can significantly help financial institutions intercept illicit activities. One predominant red flag is the sudden surge in activity, especially in newly opened accounts or those that have been dormant. Such anomalies often point toward money mule fraud, where accounts are used as temporary holding points for illegal funds.
Equally telling is the pattern of large, round-figure transactions that are inconsistent with the customer’s profile and history. This irregularity can be a harbinger of money mule activities, particularly when funds are rapidly withdrawn post-deposit. Additionally, transactions involving foreign accounts or directed to high-risk jurisdictions should prompt further scrutiny. These patterns not only indicate money mule involvement but may also be related to the broader spectrum of fincrime, including fake bank accounts and sophisticated laundering schemes.
Another red flag is the receipt of funds followed by immediate or almost immediate transfers to other accounts, especially when these transactions lack a clear lawful purpose or are inconsistent with the customer’s normal business activities. This is often a tactic employed in money mule scams, where individuals are used to move and launder stolen funds.
Moreover, frequent changes in account information – such as email addresses, phone numbers, and physical addresses – can also indicate mule accounts. These changes might indicate an attempt to evade detection, a common practice in money laundering and fraud schemes.
To discover more about money muling, including statistics and how this phenomenon makes an impact on the financial market, please explore our article: Money Muling: The Covert Conduit of Illicit Financial Flows.
What are the types of money mules?
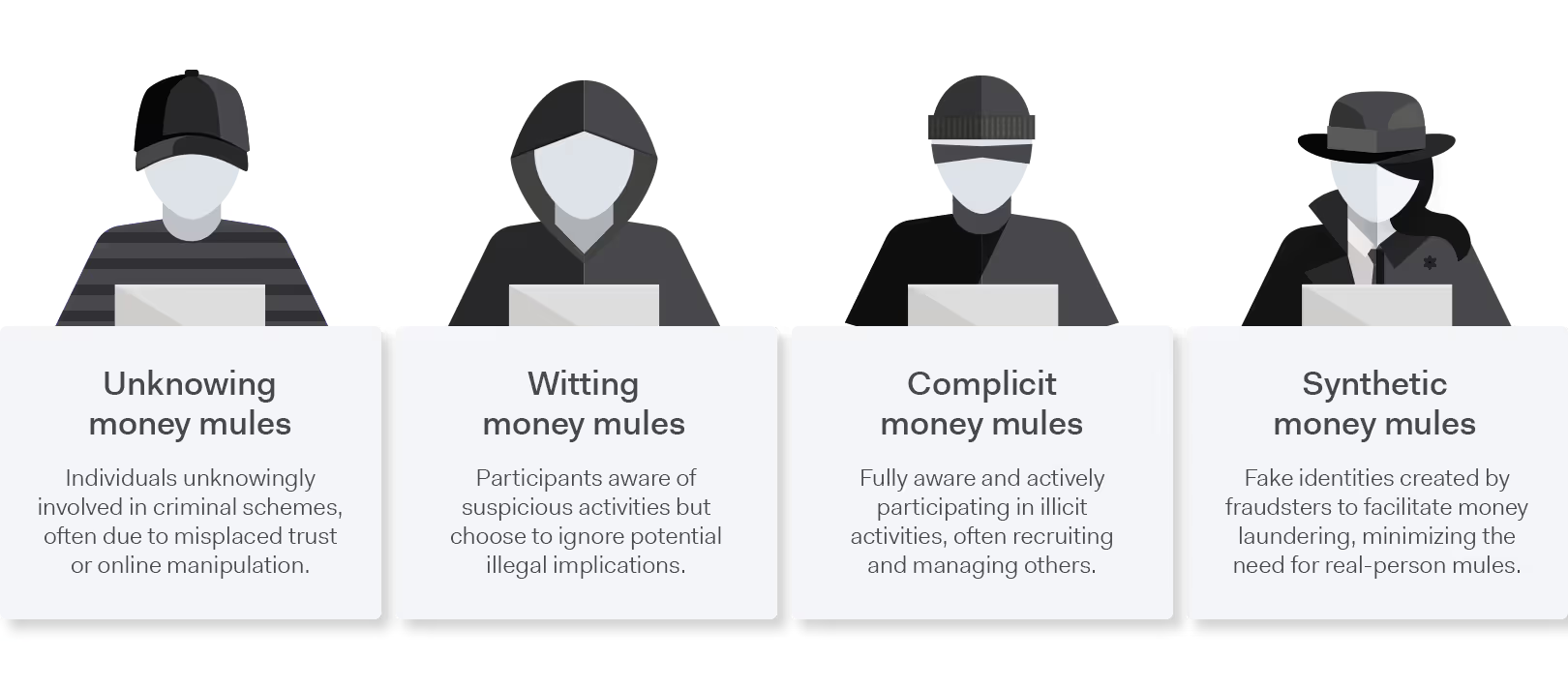
There are four different types of money mules:
- Unknowing money mules: individuals unknowingly involved in criminal schemes, often due to misplaced trust or online manipulation.
- Witting money mules: participants aware of suspicious activities but choose to ignore potential illegal implications.
- Complicit money mules: individuals fully aware and actively participating in illicit activities, often recruiting and managing others.
- Synthetic money mules: fake identities created by fraudsters to facilitate money laundering, minimizing the need for real-person mules.
As well as knowing what different types of money mules exist, financial institutions should embrace a methodical approach in monitoring transactions and online behaviors of potential money mules.
Transaction patterns and behavioral analysis in detecting money mules
Unraveling the complexities of money mule operations requires a keen understanding of specific transaction patterns and customer behaviors. One of the most revealing patterns is the emergence of fragmented transactions. This involves breaking down large sums of money into smaller, less conspicuous amounts, a method often used in money mule scams to avoid triggering financial thresholds and alerts.
Another pattern of note is the rapid movement of funds. Money mules typically do not hold onto funds for long; the speed and frequency of transfers out of an account following incoming transactions can be a critical indicator of mule activities. This is especially true when these transfers are interspersed with periods of dormancy, a tactic designed to lower the profile of the account between activities.
Behavioral analysis also plays a pivotal role in identifying potential money mules. Customers who exhibit a lack of knowledge about the origin of funds, or who are unable to provide a plausible explanation for large transactions, may be part of a money mule network. Additionally, reluctance to provide standard documentation or identification during transactions, or inconsistencies in the information provided, can represent red flags.
A nuanced aspect of behavioral analysis involves monitoring customer reactions to bank interventions. An overreaction or unusual distress to standard banking inquiries about transactions could indicate a customer's involvement, knowingly or unknowingly, in money mule fraud. Conversely, a complete lack of concern or engagement might also be a sign of a seasoned mule who is accustomed to such scrutiny.
Having a multifaceted approach to detection is a vital step forward, combining transaction analysis with behavioral insights. By understanding and recognizing these patterns, banks and financial institutions can better position themselves to intercept money mule activities before they fully materialize, protecting both their interests and those of their customers.
Advanced detection: combining traditional and digital methods
When speaking about banking security, the integration of traditional monitoring methods with advanced digital techniques provides the strongest defense against money mule operations. Traditional methods, grounded in the scrutiny of financial transactions and customer profiles, remain fundamental. However, the augmentation of these methods with digital identity intelligence can significantly elevate a bank's capacity to identify subtle and complex money mule red flags.
One key aspect of identity intelligence involves analyzing online behaviors and digital footprints. Unusual access patterns, such as logins from different geographic locations in short periods or transactions initiated from IP addresses in high-risk jurisdictions, can signal money mule activities. The use of technology to mask or alter digital identities, like the use of VPNs or consistent IP address changes, also warrants closer examination.
Another digital approach is the analysis of communication patterns. Anomalies in email or phone communication linked to banking accounts, such as frequent changes in contact details or the use of disposable email addresses, can be indicative of synthetic money mules. These are fabricated identities used to facilitate money laundering and other fincrime activities, often leaving a trail of digital clues that can be detected through sophisticated analytics.
Machine learning algorithms play a pivotal role in deciphering these digital signals. By learning from vast datasets of banking transactions and customer behaviors, these algorithms can identify patterns that would be nearly impossible for human analysts to discern. This includes detecting intricate networks of mule accounts and flagging transactions that, while individually innocuous, collectively raise suspicions.
The convergence of traditional and digital methods not only enhances the detection of money mule activities but also adapts to the continuously evolving tactics of financial criminals. As fraudsters become more sophisticated, leveraging a combination of proven banking practices and cutting-edge technology becomes indispensable in safeguarding financial institutions and their customers.
How can banks and neobanks fight money mules?
Proactivity is key in the ongoing battle against money mule operations. Banks and neobanks, armed with knowledge and tools, can take definitive steps to mitigate the risks associated with these fraudulent activities. First and foremost is implementing rigorous customer due diligence (CDD) processes. This includes thoroughly vetting new customers, regularly reviewing existing accounts, and heightened scrutiny of accounts exhibiting red flags of money mule fraud.
Education and awareness also play a crucial role. Training bank staff to recognize the signs of money mule activities, such as patterns in money mule scams or the use of fake bank accounts, empowers them to act more effectively. Additionally, educating customers about the risks and signs of being used as a money mule can prevent unwitting involvement in these schemes.
Another crucial step is the development of robust monitoring systems. These systems should be capable of detecting unusual transaction patterns, such as those commonly seen in layering money laundering activities, and flagging them for further investigation. This involves both the analysis of transaction volumes and frequencies and the monitoring of fund origins and destinations.
Lastly, collaboration with law enforcement and other financial institutions is vital. Sharing information about emerging trends in money muling can help the entire banking community stay one step ahead of criminals. This collaboration also extends to the development and refinement of industry-wide best practices for detecting and handling money mule accounts.
Identity intelligence and building your own rules
In the era of digital banking, identity intelligence has emerged as a formidable tool in identifying and combating money mule activities. This sophisticated approach goes beyond traditional analysis, harnessing the power of alternative data from various digital signals like phone, email, IP, browser, and device use. By analyzing these digital footprints, banks can uncover hidden patterns and connections that might indicate Money Muling.
The application of machine learning algorithms in identity intelligence platforms offers a significant advantage. These algorithms can process vast amounts of data, learning from each transaction and interaction to identify even the most subtle signs of money mule red flags. The ability to continually learn and adapt makes these systems incredibly effective in keeping pace with the ever-evolving tactics of financial criminals.
Identity intelligence does not replace traditional methods but rather complements them, creating a multi-layered defense strategy. Identity intelligence empowers their existing fraud prevention frameworks, so that banks can enhance their capability to detect and prevent money mule activities, safeguarding their operations and their customers from the repercussions of financial crime.
Lessons learned from money mule red flags
The fight against money mule activities is an ongoing and evolving battle in the banking industry. Identifying money mule red flags is not just a regulatory necessity; it's a critical aspect of safeguarding the financial system and protecting innocent individuals from being caught in criminal schemes. Banks and neobanks, equipped with the right knowledge, tools, and strategies, play an essential role in this endeavor.
As financial crime continues to shift, so too must the strategies employed to combat it. Continuous learning, adapting to new methods, and collaborative efforts are key to maintaining the integrity and security of the banking sector. Vigilance and proactivity are the watchwords in this ongoing effort to prevent money mule operations.
For any further advice on how to stop money muling, please reach out to our team of experts.


