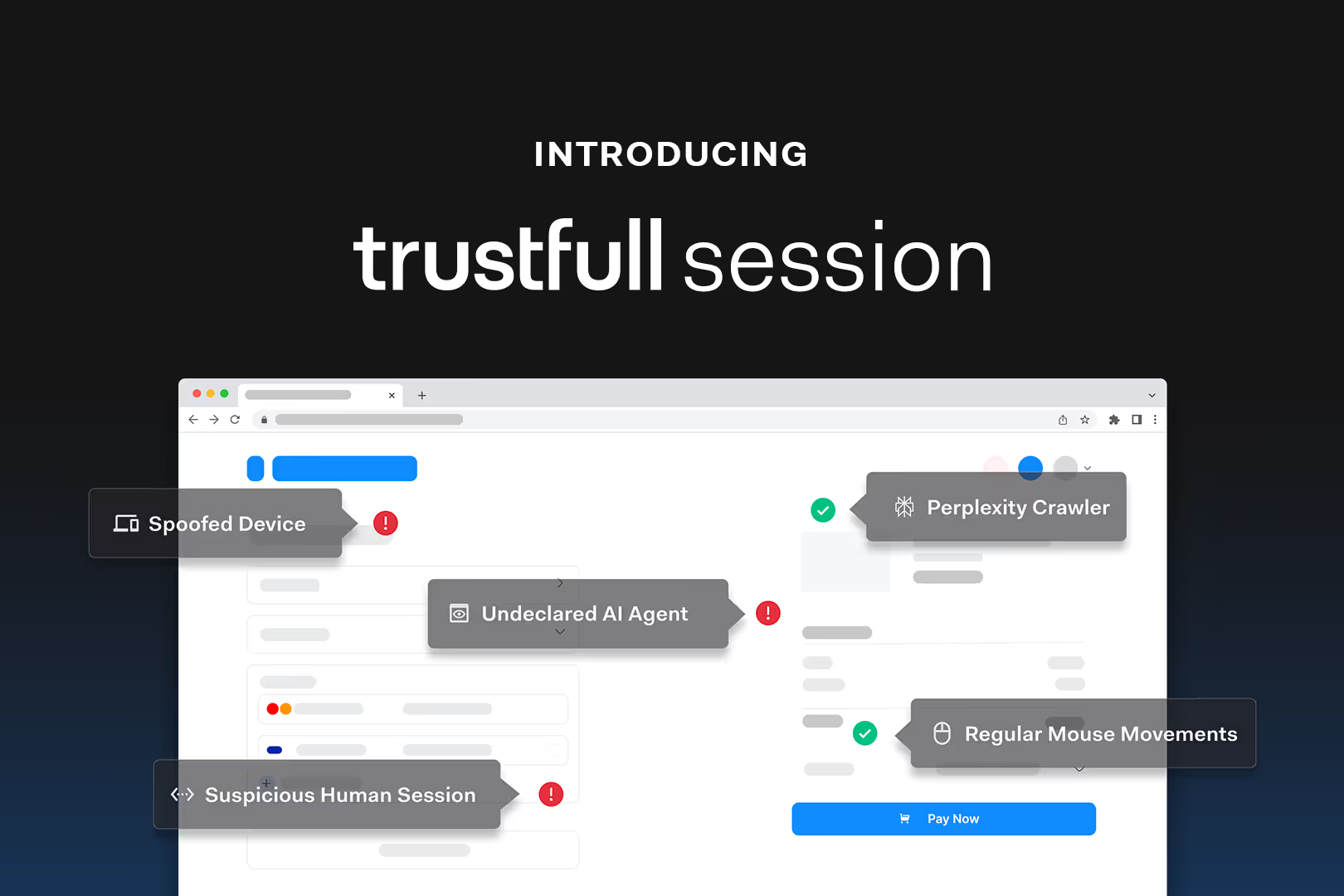
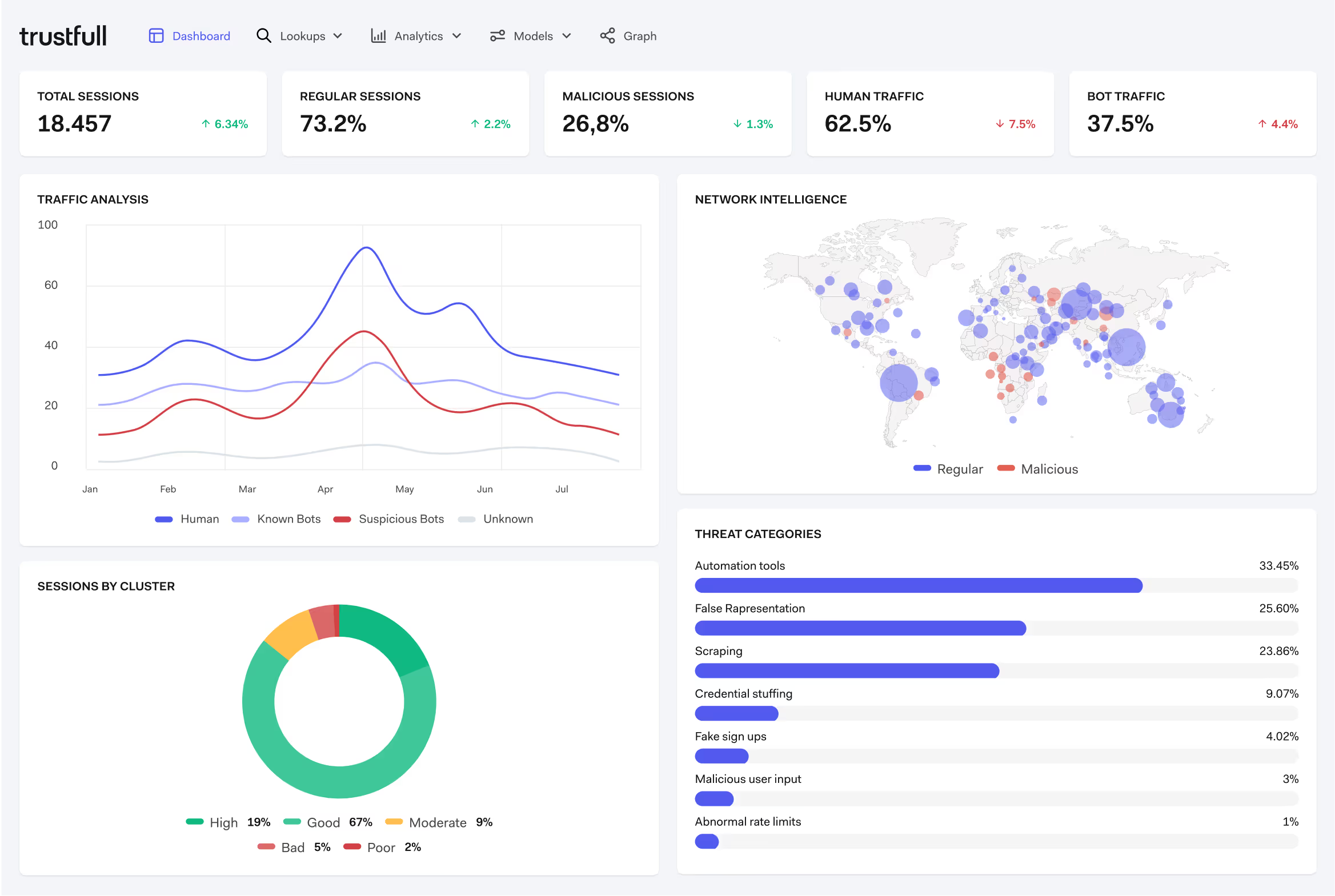
Trustfull Session
Detect malicious traffic,
human or not
Trustfull detects high-risk web sessions without disrupting real users and trusted agents, silently and in real time.
TRUSTED BY WORLD-LEADING COMPANIES












































































Next-generation session intelligence
Protect your site and APIs from bots and bad actors with silent analysis of device, browser, behavior and network signals.
Real-time
Monitor every session as it happens, detecting anomalies and threats instantly across devices and behaviors.
Fully explainable
Get clear, actionable insights into every flagged session, with transparent signal breakdowns and rule audits.
Behavior-based
Identify subtle differences in user behavior with machine learning models trained to detect abnormal patterns.
Captcha-free
No CAPTCHAs. No challenges. Just seamless defense that doesn’t get in the way of legitimate users.
Bot analysis
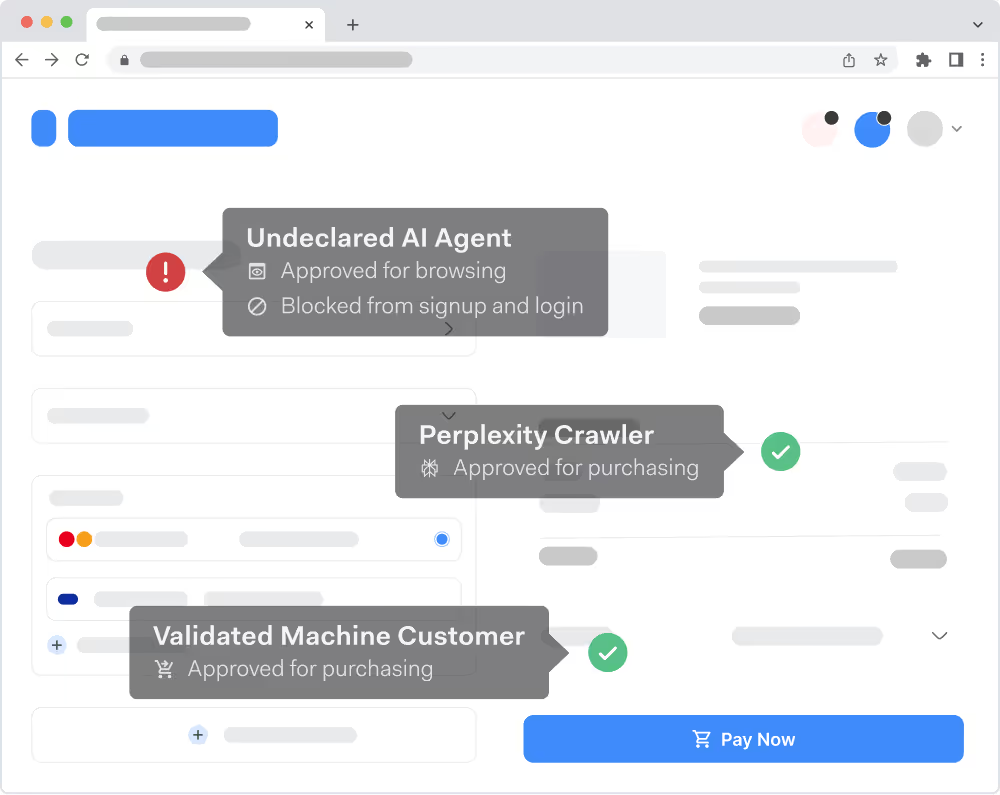
Distinguish bad bots from legitimate agents
Stay protected against bad bots while letting trusted AI agents operate safely on your platform.
Identify bots’ intent at the first point of interaction
Detect activity by hijacked or rogue agents
Classify automated traffic to spot new threats early
Behavioral biometrics
Spot malicious humans by the way they interact
Track and evaluate subtle behavioral cues to uncover patterns of deceptive activity.
Detect unusual mouse movements and velocity shifts
Flag tampering via developer console tools
Monitor abnormal click rates and traffic spikes
Browser intelligence
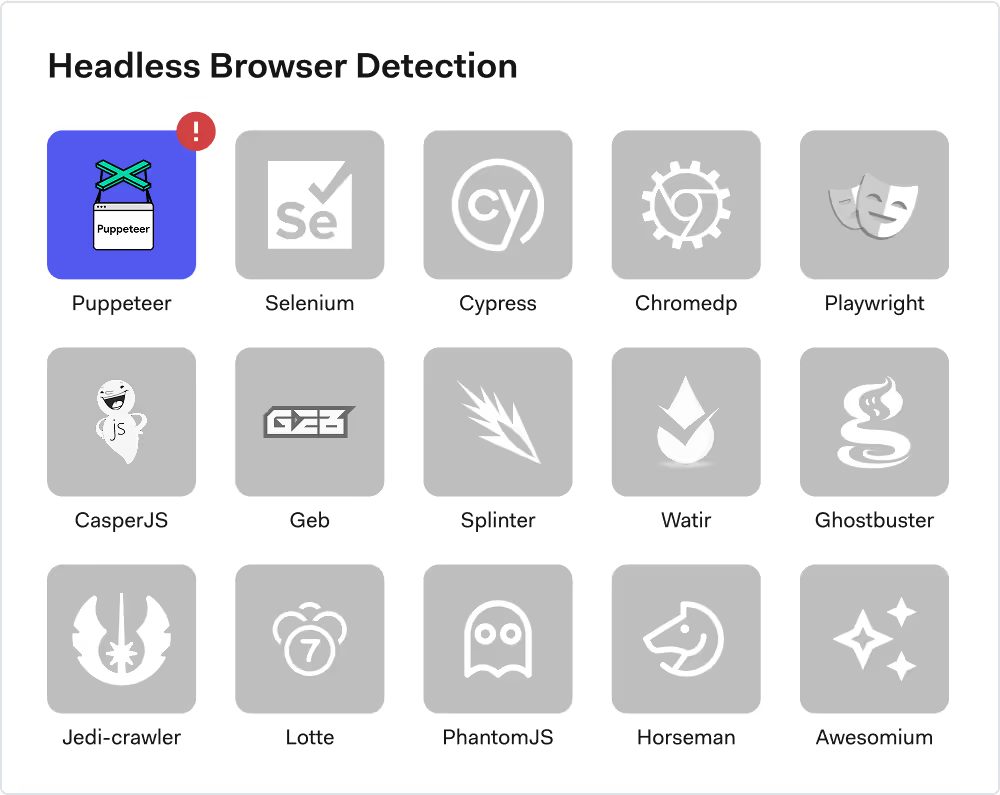
Block harmful traffic with browser analysis
Run hundreds of in-browser checks to detect anomalies and indicators of virtualization.
Collect robust fingerprint signals without cookies
Classify synthetic or misrepresented browser contexts
Detect headless browsers, emulators and virtual machines
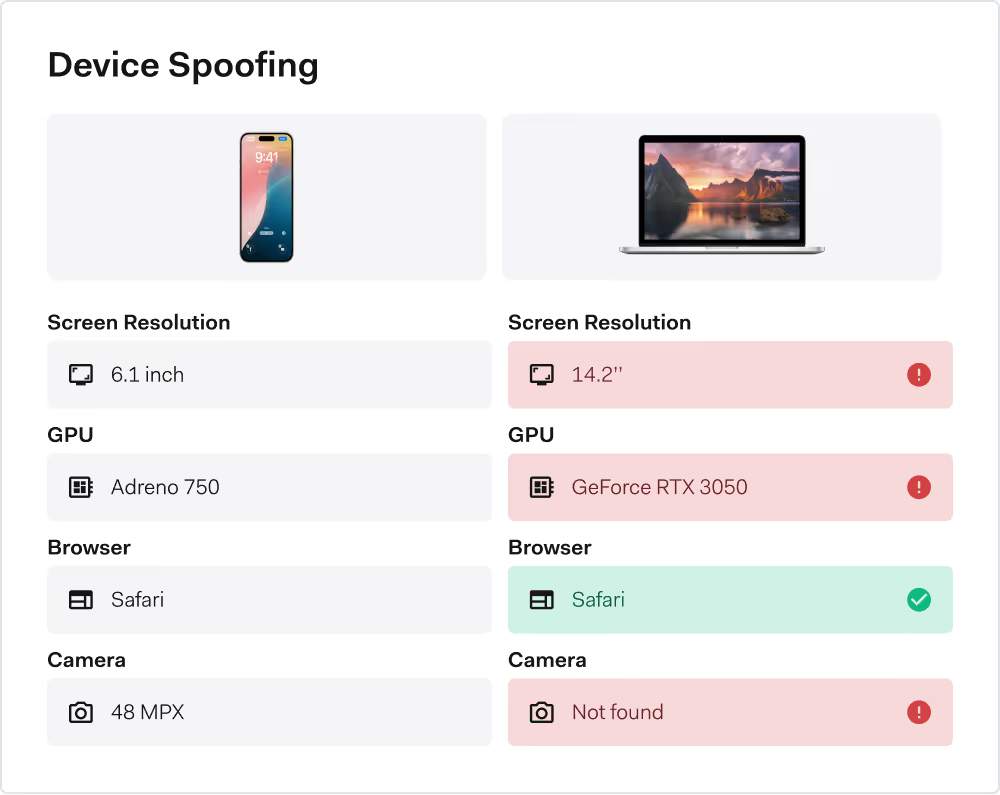
DEvice spoofing detection
Uncover device spoofing attempts in real time
Spot high-risk sessions by analyzing the type, configuration and behavior of the device in use.
Retrieve vital device information from user agent string
Verify device consistency with known configurations
Identify spoofed or cloned device characteristics
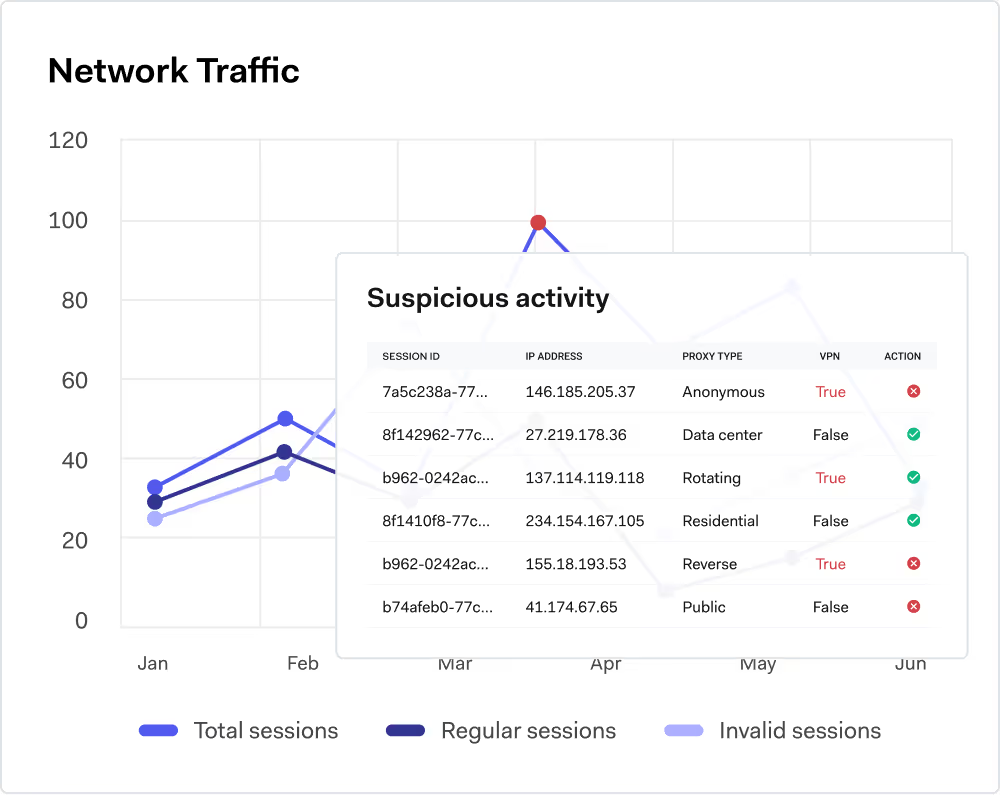
Network intelligence
Identify attackers through IP & Proxy analysis
Spot irregularities in network activity that reveal non-human behavior and suspicious web sessions.
Detect anomalies in IP reputation, ASN and geolocation
Spot usage of proxies, VPNs and datacenter IPs
Flag sudden spikes or irregular request patterns
Resources
Learn more about Trustfull Session
Detect suspicious web traffic in real time
Download our solution sheet for detailed insights into how Trustfull Session works.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
No items found.
No items found.
Want to know more?
Explore the benefits and value Trustfull brings to your company.