Article
Cross-referencing Email and Phone Data in Fraud Detection
Uros Pavlovic
August 30, 2024

Fraudsters are adept at exploiting the smallest gaps in data to bypass security measures, making it essential for businesses to equip themselves with anti-fraud measures. Various sources of information can be found through deep and careful analysis of digital signals. This furnishes organizations with a more comprehensive database of their customers, improving both their ability to detect fraud and the accuracy of their risk assessments.
Digital fraud prevention definition
Digital fraud prevention is the process of identifying and mitigating fraudulent activities that occur through online channels. Unlike traditional fraud, which might involve physical interactions, digital fraud is carried out entirely online, making it more difficult to detect and prevent. It can take many forms, including account takeovers, synthetic identity fraud, and new account fraud, all of which pose significant risks to businesses across various industries, such as financial services, fintech, betting, crypto, and online lending.
The key to effective digital fraud prevention lies in the ability to analyze digital signals—data points that can be gathered from online interactions. These signals include phone numbers, email addresses, IP addresses, device information, and more. Businesses can identify patterns and anomalies that might indicate fraudulent behavior by analyzing these signals. For example, if an email address has been linked to multiple suspicious activities, it might be flagged as high-risk.
However, simply collecting data isn't enough. The real value comes from interpreting this data, which was gathered through Open-Source Intelligence in a way that provides actionable insights. A digital risk intelligence platform can analyze these signals in real time, helping businesses to spot potential fraud before it causes significant damage. This proactive approach allows companies to not only protect themselves but also to provide a safer and more secure experience for their customers.
Phone and email fraud statistics
The number of cybercrime incidents, which includes online fraud, has greatly increased in the past few years, from approximately 467,000 in 2019 to over 880,000 in 2023. These significant increases have led to equally dramatic monetary losses. Cybercrime has caused a spike from 3.5 billion U.S. dollars to 12.5 billion U.S. dollars in financial losses (source: Statista). In the UK, for instance, a rise in cybercrime led to a £580 million loss through unauthorized and authorized fraud in 2023 (Source: UKFinance). At the center of this particular loss in the UK is a specific type of cybercrime - Authorized Push Payment (APP) fraud. Make no mistake, such crimes are easily carried out by sophisticated manipulation of personal data via phone numbers and email addresses.
Pinpointing the signs of digital fraud with digital signals
Digital signals are the breadcrumbs that fraudsters often leave behind, whether they realize it or not. Detecting fraud isn’t simple, although if you have the right tools these fraudulent activities can be avoided before they escalate. With that in mind, we’ll explore how specific digital signals like phone numbers and email addresses can be cross-referenced to verify identities and prevent fraud.
Phone to name
A phone number is more than just a means of communication; it's a valuable data point that can be used to verify a user’s identity. The concept of “phone to name” involves linking a phone number to the name of the person or entity associated with it. This is particularly useful in cases where a business has only a phone number and needs to confirm whether the name provided matches the records associated with that number.
When a digital risk intelligence platform is utilized regularly, businesses gain access to vast databases that correlate phone numbers with names, helping to identify discrepancies that might suggest fraudulent activity. For instance, if a phone number is linked to multiple names or has been used in previous fraudulent attempts, it can be flagged for further investigation.
If the name is not valid, a digital risk intelligence platform immediately flags it as a risk. Here are a few examples of results when looking at phone number signals:
- The user has a placeholder name such as John Doe.
- The name is fictional or imaginary, not representing a real entity or person.
- The invalid name is possibly a joke word or uses vulgar language.
There are numerous other possible variants; check out the full list in the Trustfull Data Catalogue.
Phone to email
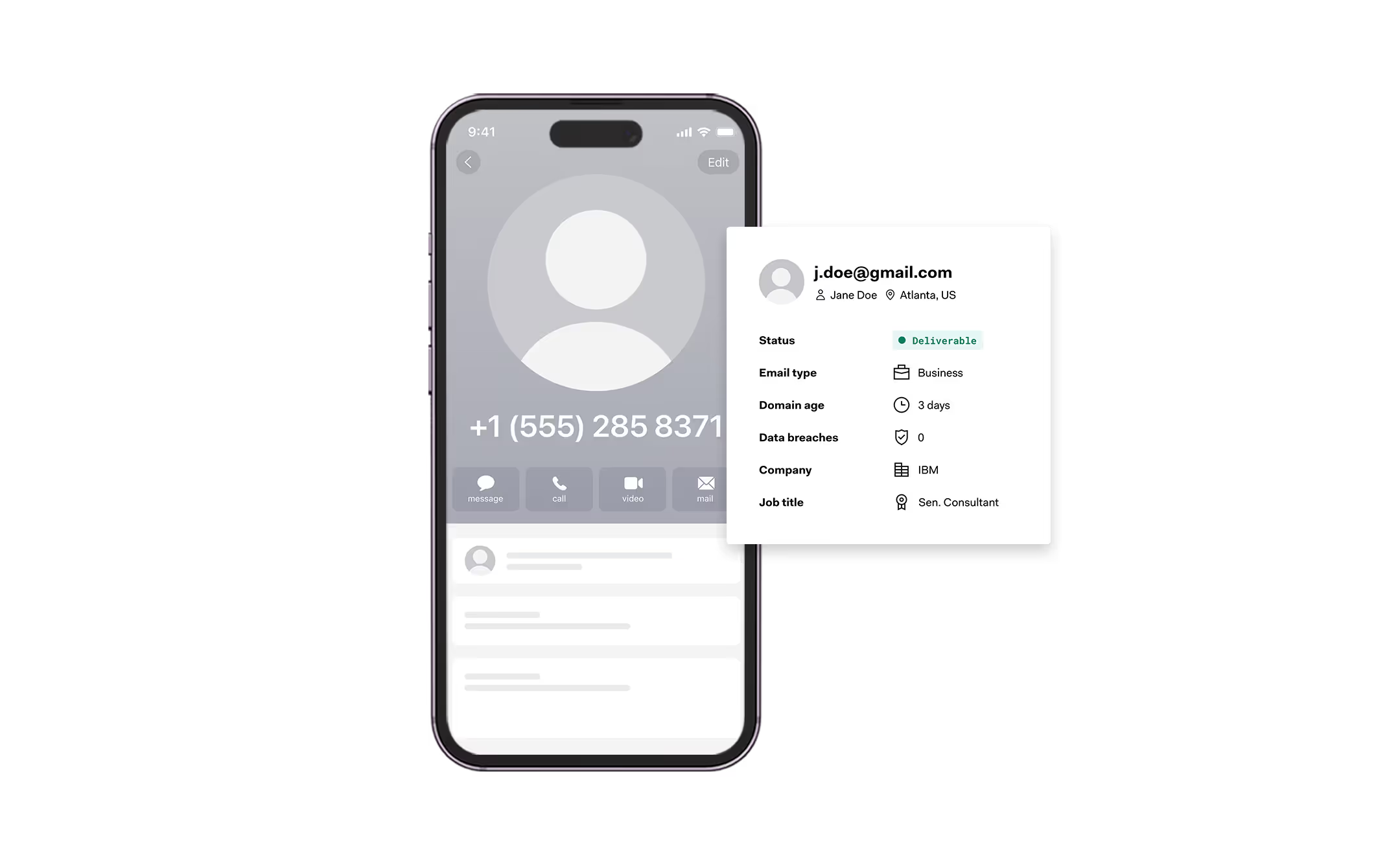
Similar to “phone to name,” the “phone to email” process involves connecting a phone number with the corresponding email address. This connection is crucial because it helps verify whether the contact information provided by a user is consistent across different channels. In fraud detection, inconsistencies between a phone number and an email address can be a red flag.
Let’s say a phone number is associated with a legitimate customer and is then suddenly linked to a new and suspicious email address, this might indicate that the account has been compromised. Such connections can be scrutinized using insights from various phone risk models or email risk models. Businesses are then alerted businesses to potential risks and can then take appropriate action. When utilizing Phone Number Intelligence, the journey towards successfully fighting fraud can be completed
Email to name
.avif)
The “email to name” link is another critical aspect of fraud detection. In this process, businesses can verify whether the name provided by a user matches the name associated with their email address. Fraudsters often use fake or stolen email addresses to create accounts, so verifying this connection is essential for maintaining security.
An email address can be cross-referenced with names, thus identifying inconsistencies that may indicate a fraudulent attempt. If an email address has been used under multiple names or if the name associated with the email does not match the one provided by the user, it could be a sign of synthetic identity fraud.
Email to phone
The “email to phone” link works in the opposite direction, verifying whether an email address corresponds to the phone number provided by the user. This is especially useful in situations where a business has an email address but lacks a phone number, or vice versa. Connecting these two data points means that businesses get a better understanding of the user’s identity and detect potential fraud. Drive up account verifications with accurate email checks, AI-driven email scoring, and deliverability analysis. Using Email Address Analytics as a silent method of detection, fake email addresses can be significantly reduced in the customer qualification process. It may also be an effective way of automating your approval process.
A digital risk intelligence platform can automate this process, quickly identifying mismatches between email addresses and phone numbers that might suggest fraudulent behavior. For example, if an email address frequently appears alongside different phone numbers, it might indicate that the address is being used for fraudulent purposes.
Digital risk intelligence: the road to fake account prevention
A huge part of the digital risk intelligence process is gathering and analyzing alternative data sources, which include phone numbers, email addresses, IP addresses, browser data, and device information. These provide a rich assortment of insights that can be woven together to create a comprehensive picture of a user's digital identity.
Trust and risk signals
Alternative data points serve as the foundation for generating trust and risk signals, which are essential for identifying potential fraud. The ability to properly interpret these signals is accessible via a digital risk intelligence platform. It’s the quickest way to uncover patterns that might be invisible to traditional detection methods. For instance, a phone number used across multiple devices or IP addresses might indicate an attempt to mask fraudulent activity, while an email address associated with a high-risk IP range could be a red flag for synthetic identity fraud.
The key to maximizing the effectiveness of these signals lies in the platform's ability to cross-reference and analyze data in real time. This dynamic approach allows businesses to stay ahead of fraudsters by detecting anomalies and inconsistencies as they arise, rather than relying solely on historical data.
The more you use risk scoring as a fraud detection method, the more you refine your internal digital onboarding process.
Capturing fraud through risk scoring models
One of the most powerful features of a digital risk intelligence platform is its ability to utilize risk scoring models. These models are designed to evaluate the likelihood of fraudulent activity based on the analysis of alternative data. Each data point—whether it’s a phone number, email address, or IP address—contributes to an overall risk score that helps businesses make informed decisions about the trustworthiness of a user.
System-generated models: these models are pre-configured based on the extensive experience of data experts and are ready to use from the moment a business signs up.
Custom models: custom models can be built from scratch or by modifying existing templates, allowing businesses to define their scoring criteria and rules.
Impact previews and backtesting: through impact previews and backtesting, businesses can evaluate how different models perform under various conditions, allowing them to choose the most effective approach for their fraud detection strategy.
The integration of risk scoring models—whether system-generated or custom-built—provides a powerful tool for evaluating the likelihood of fraudulent activities.
As digital interactions continue to grow in both scale and complexity, bridging communication gaps through the intersection of email, phone, and other data signals cannot be overstated. Companies can enhance their security measures, reduce the risk of fraud, and build a more trustworthy digital environment.
To discover how to do that through powerful phone and email intelligence solutions, in addition to trust and risk signal detection, feel free to reach out to our team of fraud experts. Or sign up on the Trustfull Digital Risk Intelligence platform and give it a go.
Questions and Answers
How can digital signals help prevent synthetic identity fraud?
Digital signals like phone numbers, email addresses, and IP data can be cross-referenced to identify inconsistencies typical of synthetic identities. For example, if a phone number is linked to multiple names or an email address is associated with high-risk IP ranges, it could indicate a synthetic identity, allowing businesses to flag and investigate further.
What role does email verification play in detecting fraudulent accounts?
Email verification helps ensure that the email address provided by a user is legitimate and not associated with previous fraudulent activities. By analyzing the email's history, and usage patterns, and cross-referencing it with other data points like phone numbers, businesses can identify and block suspicious accounts.
Can risk scoring models adapt to new fraud trends, and if so, how?
Yes, risk scoring models can be continuously updated and refined based on new data and evolving fraud tactics. By using impact previews and backtesting, businesses can adjust their models to respond to emerging threats, ensuring that they stay effective in detecting fraud over time.
How does cross-referencing phone and email data improve digital onboarding?
Cross-referencing phone and email data during digital onboarding allows businesses to verify the consistency of user information, reducing the risk of onboarding fraudulent accounts. This method helps identify mismatches and anomalies early, ensuring that only legitimate users are approved.


